-
Success
Manage your Success Plans and Engagements, gain key insights into your implementation journey, and collaborate with your CSMsSuccessAccelerate your Purchase to Value engaging with Informatica Architects for Customer SuccessAll your Engagements at one place
-
Communities
A collaborative platform to connect and grow with like-minded Informaticans across the globeCommunitiesConnect and collaborate with Informatica experts and championsHave a question? Start a Discussion and get immediate answers you are looking forCustomer-organized groups that meet online and in-person. Join today to network, share ideas, and get tips on how to get the most out of Informatica
-
Knowledge Center
Troubleshooting documents, product guides, how to videos, best practices, and moreKnowledge CenterOne-stop self-service portal for solutions, FAQs, Whitepapers, How Tos, Videos, and moreVideo channel for step-by-step instructions to use our products, best practices, troubleshooting tips, and much moreInformation library of the latest product documentsBest practices and use cases from the Implementation team
-
Learn
Rich resources to help you leverage full capabilities of our productsLearnRole-based training programs for the best ROIGet certified on Informatica products. Free, Foundation, or ProfessionalFree and unlimited modules based on your expertise level and journeySelf-guided, intuitive experience platform for outcome-focused product capabilities and use cases
-
Resources
Library of content to help you leverage the best of Informatica productsResourcesMost popular webinars on product architecture, best practices, and moreProduct Availability Matrix statements of Informatica productsMonthly support newsletterInformatica Support Guide and Statements, Quick Start Guides, and Cloud Product Description ScheduleEnd of Life statements of Informatica products
- Velocity
- Strategy
-
Solutions
-
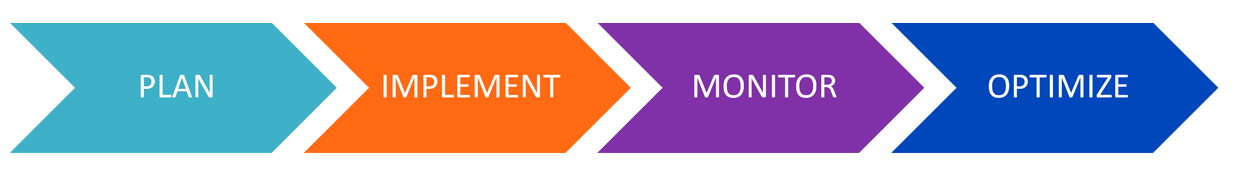
Stages
Following a rigorous methodology is key to delivering customer satisfaction and expanding analytics use cases across the business.
-
More
-
Success
Manage your Success Plans and Engagements, gain key insights into your implementation journey, and collaborate with your CSMsAccelerate your Purchase to Value engaging with Informatica Architects for Customer SuccessAll your Engagements at one place
-
Communities
A collaborative platform to connect and grow with like-minded Informaticans across the globeConnect and collaborate with Informatica experts and championsHave a question? Start a Discussion and get immediate answers you are looking forCustomer-organized groups that meet online and in-person. Join today to network, share ideas, and get tips on how to get the most out of Informatica
-
Knowledge Center
Troubleshooting documents, product guides, how to videos, best practices, and moreOne-stop self-service portal for solutions, FAQs, Whitepapers, How Tos, Videos, and moreVideo channel for step-by-step instructions to use our products, best practices, troubleshooting tips, and much moreInformation library of the latest product documentsBest practices and use cases from the Implementation team
-
Learn
Rich resources to help you leverage full capabilities of our productsRole-based training programs for the best ROIGet certified on Informatica products. Free, Foundation, or ProfessionalFree and unlimited modules based on your expertise level and journeySelf-guided, intuitive experience platform for outcome-focused product capabilities and use cases
-
Resources
Library of content to help you leverage the best of Informatica productsMost popular webinars on product architecture, best practices, and moreProduct Availability Matrix statements of Informatica productsMonthly support newsletterInformatica Support Guide and Statements, Quick Start Guides, and Cloud Product Description ScheduleEnd of Life statements of Informatica products
-
Success
Naming Conventions - Data Masking
Data Governance & Privacy
Challenge
During a Data Security/Data Masking project, rules and policies are established as an essential part of the planning process. If there are several tables (and hence several sensitive columns) involved, browsing through the objects could be troublesome. A wrong assignment of a rule or policy could seriously compromise the security of the data.
Description
A proper naming convention is very important for effectively browsing, using and tagging sensitive fields.
Rules
Rules play a key role in masking sensitive data. The following syntax can be used for naming a rule:
Syntax
rul_[Mask]_<EntityName>_[AttributeName]
Where EntityName is the name of an entity. An entity can typically be a single table or a group of related tables and AttributeName is the name of the column that is being masked.
Examples
- rul_Mask_Customer_Cust_ID
- rul_Mask_Customer_Last_Name
- rul_Mask_Customer_Addr_Line_1
Note: In the above examples, Last Name (Last_Name) and Address Line 1 (Addr_Line_1) might be attributes in two different tables belonging to “Customer” and are hence named similarly.
Policies
A policy is typically a collection of rules. The following syntax can be used for naming a Policy:
Syntax
pol_[Mask]_<EntityName>
Where EntityName is name of an entity. An entity can typically be a single table or a group of related tables.
Examples
- pol_Mask_Customer may include several tables like Customer_Names, Customer_Address, etc…
- pol_Mask_Accounts
- pol_Mask_Transactions
Plans
A plan is an executable unit. The following syntax can be used for naming a plan:
Syntax
pln_[Mask]_<EntityName>
Where EntityName is name of an entity. An entity can typically be a single table or a group of related tables.
Examples
- pln_Mask_Customer
- pln_Mask_Accounts
- pln_Mask_Transactions
Projects
A project is a workspace where metadata is imported into, and where masking, subset, and data generation artifacts can be built. The following syntax can be used for naming a Project:
Syntax
Proj_<Name of the Application>
Examples
- Proj_HR
- Proj_ODS
- Proj_Claims
