-
Success
Manage your Success Plans and Engagements, gain key insights into your implementation journey, and collaborate with your CSMsSuccessAccelerate your Purchase to Value engaging with Informatica Architects for Customer SuccessAll your Engagements at one place
-
Communities
A collaborative platform to connect and grow with like-minded Informaticans across the globeCommunitiesConnect and collaborate with Informatica experts and championsHave a question? Start a Discussion and get immediate answers you are looking forCustomer-organized groups that meet online and in-person. Join today to network, share ideas, and get tips on how to get the most out of Informatica
-
Knowledge Center
Troubleshooting documents, product guides, how to videos, best practices, and moreKnowledge CenterOne-stop self-service portal for solutions, FAQs, Whitepapers, How Tos, Videos, and moreVideo channel for step-by-step instructions to use our products, best practices, troubleshooting tips, and much moreInformation library of the latest product documentsBest practices and use cases from the Implementation team
-
Learn
Rich resources to help you leverage full capabilities of our productsLearnRole-based training programs for the best ROIGet certified on Informatica products. Free, Foundation, or ProfessionalFree and unlimited modules based on your expertise level and journeySelf-guided, intuitive experience platform for outcome-focused product capabilities and use cases
-
Resources
Library of content to help you leverage the best of Informatica productsResourcesMost popular webinars on product architecture, best practices, and moreProduct Availability Matrix statements of Informatica productsMonthly support newsletterInformatica Support Guide and Statements, Quick Start Guides, and Cloud Product Description ScheduleEnd of Life statements of Informatica products
- Velocity
- Strategy
-
Solutions
-
Stages
Following a rigorous methodology is key to delivering customer satisfaction and expanding analytics use cases across the business.
-
More
-
Success
Manage your Success Plans and Engagements, gain key insights into your implementation journey, and collaborate with your CSMsAccelerate your Purchase to Value engaging with Informatica Architects for Customer SuccessAll your Engagements at one place
-
Communities
A collaborative platform to connect and grow with like-minded Informaticans across the globeConnect and collaborate with Informatica experts and championsHave a question? Start a Discussion and get immediate answers you are looking forCustomer-organized groups that meet online and in-person. Join today to network, share ideas, and get tips on how to get the most out of Informatica
-
Knowledge Center
Troubleshooting documents, product guides, how to videos, best practices, and moreOne-stop self-service portal for solutions, FAQs, Whitepapers, How Tos, Videos, and moreVideo channel for step-by-step instructions to use our products, best practices, troubleshooting tips, and much moreInformation library of the latest product documentsBest practices and use cases from the Implementation team
-
Learn
Rich resources to help you leverage full capabilities of our productsRole-based training programs for the best ROIGet certified on Informatica products. Free, Foundation, or ProfessionalFree and unlimited modules based on your expertise level and journeySelf-guided, intuitive experience platform for outcome-focused product capabilities and use cases
-
Resources
Library of content to help you leverage the best of Informatica productsMost popular webinars on product architecture, best practices, and moreProduct Availability Matrix statements of Informatica productsMonthly support newsletterInformatica Support Guide and Statements, Quick Start Guides, and Cloud Product Description ScheduleEnd of Life statements of Informatica products
-
Success
IDD BPM Adaptor Roles Checklist
Challenge
Because there are many components included in an ActiveVOS BOM implementation, all of the necessary pieces need to be in place in order for a user to be able to create and edit tasks. A checklist should be followed to ensure the most efficient setup. A checklist can help to clarify requirements and serve as documentation for decisions that are made. As a general rule, checklists are a good way to ensure adherence to best practices.
Description
The checklist below can be used to ensure that Identities and the ActiveVOS adaptor are set up correctly for MDM/IDD and the ActiveVOS adaptor, and consequently, that ActiveVOS IDD tasks are created correctly in ActiveVOS and show up correctly in IDD.
Prerequisites
- MDM is installed
- ActiveVOS is installed
Checklist
| 1 | Is the identity service enabled? |
| 2 | Are all required roles available in ActiveVOS? |
| 3 | Does the user have all needed role(s)? |
| 4 | Can the user access ActiveVOS central? |
| 5 | Can MDM access the bpm adaptor? |
| 6 | Is the IDD task set up correctly? |
| 7 | Is the ActiveVOS Project deployed? |
| 8 | Can the user log onto IDD? |
Operation
The following items should be checked after the project is deployed and ready for testing
| 1 | Can the user get a task list? |
| 2 | Can the user create a task in IDD? |
| 3 | Does the create task work? |
| 4 | Is the task process correctly created? |
| 5 | Are tasks created correctly in the ActiveVOS process? |
| 6 | Can the user see the task in IDD? |
Is the Identity Service Enabled?
The identity service is set up on the ActiveVOS Console. Ensure that the Identity Service is set to enabled and that there are no errors.
[Server:Port]/activevos/idas_service.action.
For additional help contact Informatica support.
Are All Required Roles Available in ActiveVOS?
First make a list of all the required roles for the Application. Add abTaskClient if a role is not part of the list. Add abServiceConsumer if the server is a secured server.
Once the identity service is set up and valid, check which roles are available using the Identity Service API.
[server:port]/active-bpel/services/AeIdentityService
Calling the findRoles operation will provide a list of roles.
Request:
<iden:emptyElement xmlns:iden="http://docs.active-endpoints/wsdl/identity/2007/03/identity.wsdl"/>
Sample response
<aeidsvc:roleList xmlns:aeidsvc="http://docs.active-endpoints/wsdl/identity/2007/03/identity.wsdl">
<aeidsvc:role>updaters</aeidsvc:role>
<aeidsvc:role>approvers</aeidsvc:role>
<aeidsvc:role>ApprobateurRepere</aeidsvc:role>
<aeidsvc:role>publishers</aeidsvc:role>
<aeidsvc:role>PropietaireUP</aeidsvc:role>
<aeidsvc:role>admin</aeidsvc:role>
<aeidsvc:role>loanreps</aeidsvc:role>
<aeidsvc:role>abTaskClient</aeidsvc:role>
<aeidsvc:role>InteriorSpecialistGroup</aeidsvc:role>
</aeidsvc:roleList>
Ensure that all required roles are in the list.
Does the User Have All Needed Roles?
Ensure that each user has the needed role(s) using the Identity Service API.
[server:port]/active-bpel/services/AeIdentityService.
Call thefindRolesByPrincipal operation for each user to determine whether the correct roles are in place.
Note: Other operations can provide all the details in one response (and this can be for users or values can be checked in the underlying Identity resource). This is an example of how to check that a user has the correct role.
Sample Request
<iden:principalName xmlns:iden="http://docs.active-endpoints/wsdl/identity/2007/03/identity.wsdl">loanrep1</iden:principalName>
Sample Response
<aeidsvc:roleList xmlns:aeidsvc="http://docs.active-endpoints/wsdl/identity/2007/03/identity.wsdl">
<aeidsvc:role>LoanNegotiator</aeidsvc:role>
<aeidsvc:role>loanreps</aeidsvc:role>
<aeidsvc:role>abTaskClient</aeidsvc:role>
</aeidsvc:roleList>
Can the User Access ActiveVOS Central?
In some cases the Identity Service is not based on the same mechanism as the service authorization. This means the user must be able to access the server as well as have the necessary ActiveVOS roles. A good way to check this is to log into ActiveVOS central as the user. This will confirm that the user can access the Application server as well as the inbox. For each user go to [Server:Port]/activevos-central and log on with the user’s credentials.
Can MDM Access the bpm Adaptor?
The configuration of the workflow adaptor is set up in MDM. The server needs to be exposed as http and not https. Enter the Host, Port, Username and Password that are needed to access the ActiveVOS server.
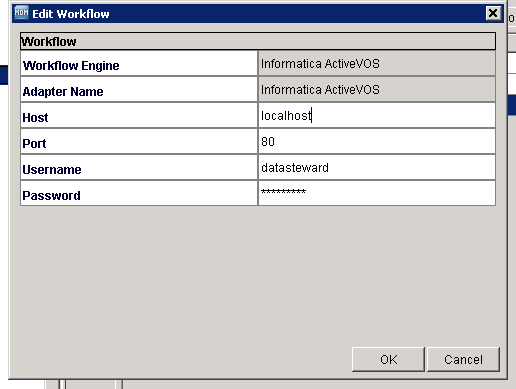
Test the connection to ensure that it works.
Is the IDD Task Set up Correctly?
The IDD task is set up in the IDD config.
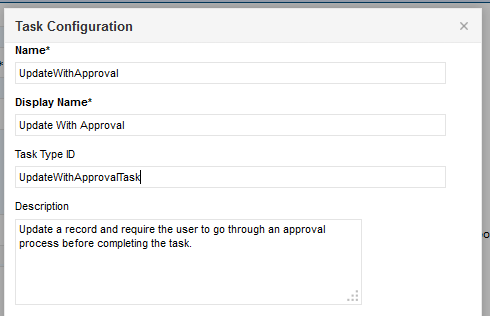
Ensure that the task is set up for the correct subjectAreaUID and functionality. Make sure that the Task Type ID matches the service that is deployed in ActiveVOS (see next step). Make a list of all task Type IDs and what they are used for.
Is the ActiveVOS Project Deployed?
Each task set up has a Task Type ID. Make sure that this is available on the ActiveVOS server. Go to [SERVER:PORT]/activevos/deployed_services.action and check that a Service with the same name as the Task Type ID is present.
Sample from the service Definition page.


Can the User Log Onto IDD?
For each user that will create or edit tasks the user needs to access IDD. Go to [server:PORT]/bdd/login.jsf and log in with the username and password.
Can the User Get a Task List?
Does the IDD task list screen work without errors?
Can the User Create a Task?
Does the approval icon appear?
Does the Create Task Work?
Is the user able to create a task successfully without an error?
Is the Task Process Correctly Created?
Check that the running workflow is visible on the ActiveVOS server.
