-
Success
Manage your Success Plans and Engagements, gain key insights into your implementation journey, and collaborate with your CSMsSuccessAccelerate your Purchase to Value engaging with Informatica Architects for Customer SuccessAll your Engagements at one place
-
Communities
A collaborative platform to connect and grow with like-minded Informaticans across the globeCommunitiesConnect and collaborate with Informatica experts and championsHave a question? Start a Discussion and get immediate answers you are looking forCustomer-organized groups that meet online and in-person. Join today to network, share ideas, and get tips on how to get the most out of Informatica
-
Knowledge Center
Troubleshooting documents, product guides, how to videos, best practices, and moreKnowledge CenterOne-stop self-service portal for solutions, FAQs, Whitepapers, How Tos, Videos, and moreVideo channel for step-by-step instructions to use our products, best practices, troubleshooting tips, and much moreInformation library of the latest product documentsBest practices and use cases from the Implementation team
-
Learn
Rich resources to help you leverage full capabilities of our productsLearnRole-based training programs for the best ROIGet certified on Informatica products. Free, Foundation, or ProfessionalFree and unlimited modules based on your expertise level and journeySelf-guided, intuitive experience platform for outcome-focused product capabilities and use cases
-
Resources
Library of content to help you leverage the best of Informatica productsResourcesMost popular webinars on product architecture, best practices, and moreProduct Availability Matrix statements of Informatica productsMonthly support newsletterInformatica Support Guide and Statements, Quick Start Guides, and Cloud Product Description ScheduleEnd of Life statements of Informatica products
- Velocity
- Strategy
-
Solutions
-
Stages
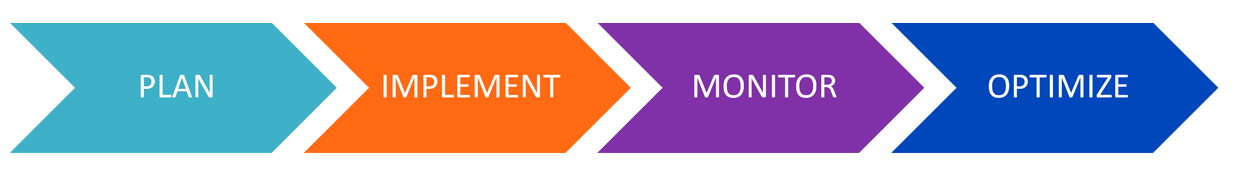
Following a rigorous methodology is key to delivering customer satisfaction and expanding analytics use cases across the business.
-
More
-
Success
Manage your Success Plans and Engagements, gain key insights into your implementation journey, and collaborate with your CSMsAccelerate your Purchase to Value engaging with Informatica Architects for Customer SuccessAll your Engagements at one place
-
Communities
A collaborative platform to connect and grow with like-minded Informaticans across the globeConnect and collaborate with Informatica experts and championsHave a question? Start a Discussion and get immediate answers you are looking forCustomer-organized groups that meet online and in-person. Join today to network, share ideas, and get tips on how to get the most out of Informatica
-
Knowledge Center
Troubleshooting documents, product guides, how to videos, best practices, and moreOne-stop self-service portal for solutions, FAQs, Whitepapers, How Tos, Videos, and moreVideo channel for step-by-step instructions to use our products, best practices, troubleshooting tips, and much moreInformation library of the latest product documentsBest practices and use cases from the Implementation team
-
Learn
Rich resources to help you leverage full capabilities of our productsRole-based training programs for the best ROIGet certified on Informatica products. Free, Foundation, or ProfessionalFree and unlimited modules based on your expertise level and journeySelf-guided, intuitive experience platform for outcome-focused product capabilities and use cases
-
Resources
Library of content to help you leverage the best of Informatica productsMost popular webinars on product architecture, best practices, and moreProduct Availability Matrix statements of Informatica productsMonthly support newsletterInformatica Support Guide and Statements, Quick Start Guides, and Cloud Product Description ScheduleEnd of Life statements of Informatica products
-
Success
Security Manager
Cloud Data Warehouse & Data Lake
The Security manager is responsible for defining and ensuring adherence to security policies and standards within the Enterprise Information Technology (IT) environment and works to develop security policies and guidelines in conjunction with application and process owners. The Security Manager is responsible for promoting organizational security awareness and advising management about security issues and potential threats. He/she may also carry out risk analysis activities. It is important that the Security Manager be current on the latest security problems/risks/resolutions. Interacting with partner companies and security organizations to share ideas around security issues is highly recommended.
Responsibilities
- Develops enterprise security standards and policies
- Makes recommendations to achieve operational and project goals in conjunction with security requirements and best practices
- Monitors and assesses security vulnerabilities across technical disciplines
- Acts as a subject matter expert for the technical security arena
- Provides advisory services to direct reports, security team members and the business
- Serves as an escalation point for security related issues and works to resolve security risks and to minimize potential threats
- Researches and stays current on new and evolving technologies and associated security risks
- Develops security tools and utilities that may be leveraged by the organization
- Reviews security specific change requests and provides risk assessments for changes
- Builds and maintains relationships with peer security professionals
Qualifications/Certifications
- Experience in the IT security sector
- Ability to lead and manage technical staff
- Capable of designing and implementing state-of-the-art security services
- Experience providing advisory services in the area of technology and security architecture
- Broad understanding of computer and communication systems and networks and their interrelationships
- Strong task and project management skills with the ability to manage parallel work streams
- Good understanding of privacy and regulatory laws, their implications, and mitigating measures
- CISSP or related certification
