-
Manage your Success Plans and Engagements, gain key insights into your implementation journey, and collaborate with your CSMsSuccessAccelerate your Purchase to Value by engaging with Informatica for Customer SuccessAll your Engagements at one place
-
A collaborative platform to connect and grow with like-minded Informaticans across the globeCommunitiesConnect and collaborate with Informatica experts and championsHave a question? Start a Discussion and get immediate answers you are looking forCustomer-organized groups that meet online and in-person. Join today to network, share ideas, and get tips on how to get the most out of Informatica
-
Troubleshooting documents, product guides, how to videos, best practices, and moreKnowledge CenterOne-stop self-service portal for solutions, FAQs, Whitepapers, How Tos, Videos, and moreVideo channel for step-by-step instructions to use our products, best practices, troubleshooting tips, and much moreInformation library of the latest product documentsBest practices and use cases from the Implementation team
-
Rich resources to help you leverage full capabilities of our productsLearnRole-based training programs for the best ROIGet certified on Informatica products. Free, Foundation, or ProfessionalFree and unlimited modules based on your expertise level and journeySelf-guided, intuitive experience platform for outcome-focused product capabilities and use cases
-
Library of content to help you leverage the best of Informatica productsResourcesMost popular webinars on product architecture, best practices, and moreProduct Availability Matrix statements of Informatica productsMonthly support newsletterInformatica Support Guide and Statements, Quick Start Guides, and Cloud Product Description ScheduleEnd of Life statements of Informatica productsMonitor the status of your Informatica services across regions
Cloud Data Access Management
Unlock Cloud Data Securely and Seamlessly
The Informatica Cloud Secure Agent is a lightweight program that runs all tasks and enables secure communication across the firewall between your organization and Informatica Intelligent Data Management Cloud (IDMC) Services. When the Secure Agent runs a task, it connects to the Informatica Cloud hosting facility to access task information. It connects directly and securely to sources and targets, transfers data between them, orchestrates the flow of tasks, runs processes, and performs any additional task requirement.



Enabling Data Access Management in CDGC lets you create metadata-driven policies to control and protect data access across integration, marketplace, and cloud platforms - ensuring safe, compliant, and efficient data use.



Data classification is the process of identifying and organizing data into relevant categories based on the functional meaning of data. Classifying data can help your organization manage risks, compliance, and data security. Additionally, Data Classifications determine the data protection applied to the mapped data element (i.e. Database Column).



A Business Glossary defines terms to ensure consistent language and reduce miscommunication across an organization.
A Data Taxonomy organizes these terms hierarchically into domains and subdomains for specific purposes.



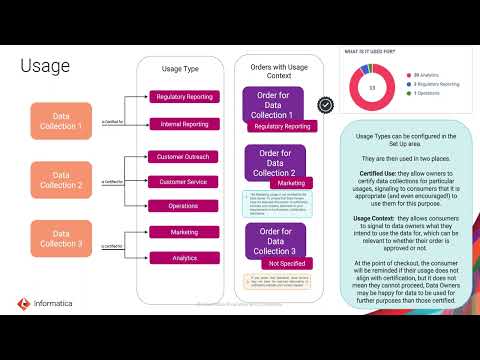
Usage Types are used to define the condition on when data access controls apply to a data request. Data Users and stakeholders to specify the contexts around data usage.



Configure scanners to extract metadata from Catalog Sources in the Metadata Command Center. Data Protections will be applied on the Catalog Sources.





Learn how to curate data classifications in the cloud by identifying sensitive data, leveraging data discovery features, and configuring rules to classify and govern your data effectively. This approach helps your organization enhance risk management, ensure compliance, and strengthen data security.





Use the Glossary Association feature in the catalog source to automatically associate glossary terms with technical assets or receive recommendations for manual association in Data Governance and Catalog.
If you want to look at how your data in the catalog is structured and wish to explore data by asset types, you can do so from the Browse page. Here, you can access both business and technical assets, including Glossary, Policy, System, Process, and Data Catalog.
When you browse an asset, you can easily drill down to see child assets that are associated with the asset.


Precedence Tiers allow for a grouping of Data De-Identification policies, helping manage and organize these policies and their enforcements.
Protections define a specific privacy enhancing technique, behavior, that is applied to data. Protections include the ability to redact, retain, generalize, replace or mask data.

Stay informed about upcoming expert-led webinars to enhance your skills in cloud data access management and secure your organization’s valuable data - View upcoming webinars
