-
Manage your Success Plans and Engagements, gain key insights into your implementation journey, and collaborate with your CSMsSuccessAccelerate your Purchase to Value by engaging with Informatica for Customer SuccessAll your Engagements at one place
-
A collaborative platform to connect and grow with like-minded Informaticans across the globeCommunitiesConnect and collaborate with Informatica experts and championsHave a question? Start a Discussion and get immediate answers you are looking forCustomer-organized groups that meet online and in-person. Join today to network, share ideas, and get tips on how to get the most out of Informatica
-
Troubleshooting documents, product guides, how to videos, best practices, and moreKnowledge CenterOne-stop self-service portal for solutions, FAQs, Whitepapers, How Tos, Videos, and moreVideo channel for step-by-step instructions to use our products, best practices, troubleshooting tips, and much moreInformation library of the latest product documentsBest practices and use cases from the Implementation team
-
Rich resources to help you leverage full capabilities of our productsLearnRole-based training programs for the best ROIGet certified on Informatica products. Free, Foundation, or ProfessionalFree and unlimited modules based on your expertise level and journeySelf-guided, intuitive experience platform for outcome-focused product capabilities and use cases
-
Library of content to help you leverage the best of Informatica productsResourcesMost popular webinars on product architecture, best practices, and moreProduct Availability Matrix statements of Informatica productsMonthly support newsletterInformatica Support Guide and Statements, Quick Start Guides, and Cloud Product Description ScheduleEnd of Life statements of Informatica productsMonitor the status of your Informatica services across regions
- Solution Accelerators
- California Consumer Privacy Act
As of January 2020, California Consumer Privacy Act (CCPA) took effect granting consumers the right to the collection, use, and sale of their data. The act poses lots of questions and distinct challenges and you must look at data security and data governance across your enterprise.
With every challenge, there arises a new opportunity. Our CCPA Accelerator powered by Informatica’s deep expertise in Data Management and Data governance will help you utilize this opportunity and help you in your goal towards compliance.
Our CCPA Accelerator provides Informatica Data Privacy Framework with prefilled templates to showcase how sensitive data moves across the onboarding process. We offer exercises with another tool called Data Privacy Management (DPM) to check whether sensitive data is protected. We cover main use cases like Subject Rights Requests (SRR), Data Subject Access Request (DSAR), Right To Be Forgotten (RTBF), and Right to Rectification. We have configured our CCPA Accelerator to help you create a clearly defined plan to achieve compliance.
This CCPA Accelerator powered by Informatica’s deep expertise in Data Management and Data governance helped you in your goal towards compliance.
The CCPA Accelerator provided Informatica Data Privacy Framework with prefilled templates to showcase how sensitive data moves across the onboarding process. We offered exercises with another tool called Data Privacy Management (DPM) to check whether sensitive data is protected. We covered main use cases like Subject Rights Requests (SRR), Data Subject Access Request (DSAR), Right To Be Forgotten (RTBF), and Right to Rectification. We have configured our CCPA Accelerator to help you create a clearly defined plan to achieve compliance.
Contents

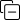
Hardly anything is more ubiquitous these days than data. Air and water may be more prevalent, but not much else. That’s certainly not a bad thing, because the world has benefited tremendously from the ability to collect, process, analyze, and share data, and use it to provide personalized and powerful services to customers and businesses. But this prevalence of data brings plenty of risks, too, including unwelcome privacy intrusions and nefarious breaches.
Not surprisingly, people are demanding more control over the personal data related to them. That’s a big part of what’s driving the new California Consumer Privacy Act (CCPA), enacted by the California State Legislature with an effective date in January 2020. It’s requiring businesses around the world — not only in California — to take a fresh look at how they handle data on individuals. It’s even forcing new thinking on what constitutes sensitive or personal data.
All businesses everywhere need to explore the ramifications of the CCPA because it affects many organizations that may not expect it. The price of ignoring this compliance minefield is potentially high. The good news is: Getting ahead of the curve can provide benefits that go well beyond the satisfaction of simply living within the law.
Disclaimer:
The CCPA accelerator is an example-based content and may differ from organization to organization. Especially, Regulation and Policy Contents may not be up to date with the latest amendments from the legislature, and policies listed are generic and may have to be customized by your Legal Team as it's written in response to the Regulation. This book is not intended to convey, does not include, and should not be relied on as legal advice.
This book consists of half a dozen chapters, each of which focuses on a topic related to the CCPA and the approach your organization should consider taking to deal with it. Here’s a glimpse:
- Chapter 1: “How to Adopt CCPA”: What is CCPA anyway, who does it affect, and how? What does it require, who’s overseeing it, who can help? And, is there perhaps a silver lining?
- Chapter 2: “Insights into What Data is Affected”: All kinds of different data types exist out there, some that fall under the watchful eye of the CCPA and some that don’t. How can you tell the difference, and what kind of governance will help you deal with the challenge?
- Chapter 3: “Discovering the Data”: The larger your organization, the more places in-scope data may be stored (or hiding). You need to find all the in-scope data, assess the risks each data store poses, and figure out how to minimize those risks.
- Chapter 4: “Manage Risk and Compliance”: CCPA underscores the need to keep prying eyes from gaining access to data they should not see. How can you gain the required control?
- Chapter 5: “Accelerate CCPA Journey”: The CCPA Accelerator has prefilled templates with sample data to showcase how “Sensitive Data” moves across the Onboarding Process. Each template defines the facets and relationships between the facets. It mainly concentrates on importing the CCPA regulation body and policies related to the CCPA. Facets that are targeted for this accelerator are Glossary, Regulation, Policy, System, Datasets, Attributes, People, etc.
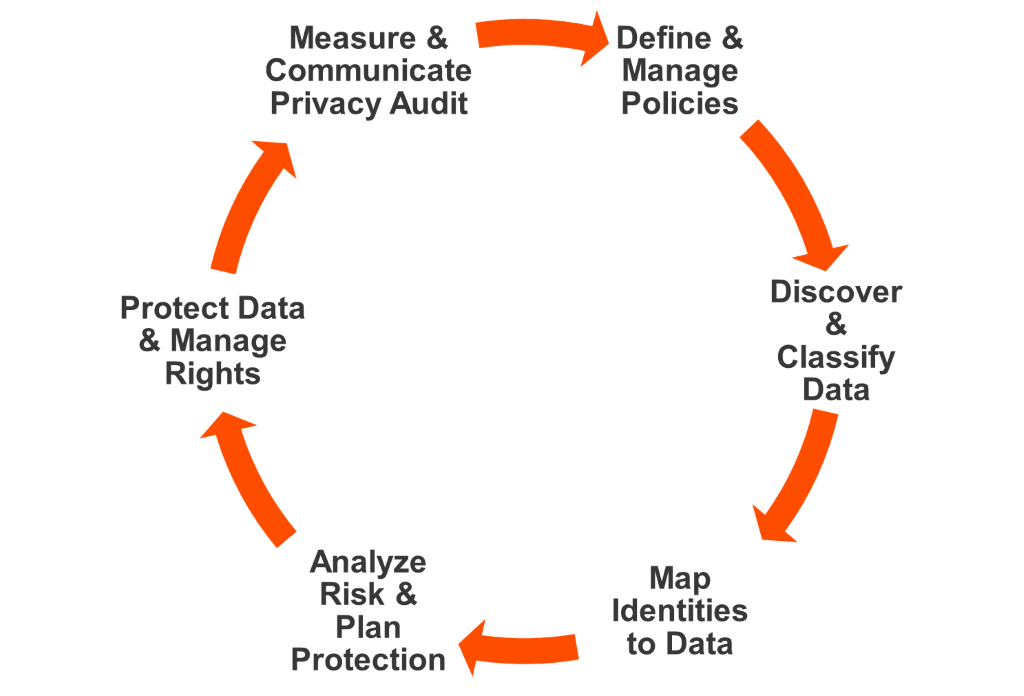
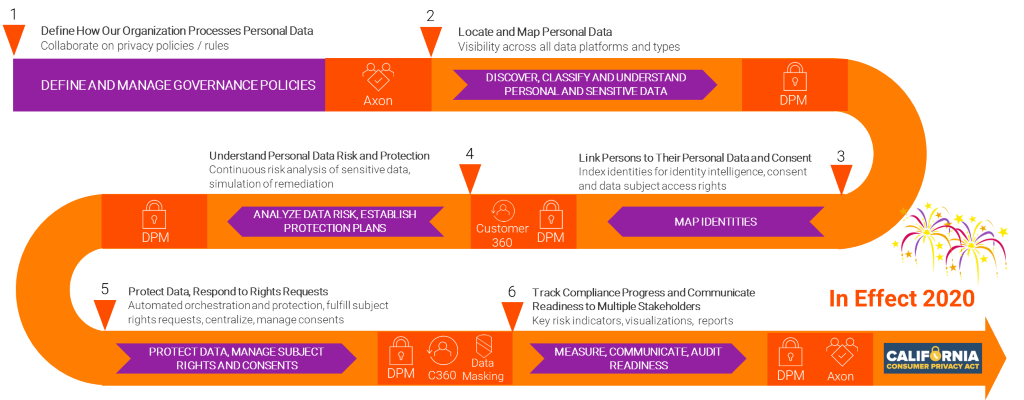
Leverage Informatica Data Privacy Framework - A continuous journey to scale privacy governance and reduce risk!
Figure 1. Informatica Data Privacy Network

The California Consumer Privacy Act (CCPA) grants consumers rights related to the collection, use, and sale of their personal data—and prevents businesses from discriminating against them for exercising those rights. It applies to organizations that do business in California if they meet specific requirements. The CCPA took effect on January 1, 2020. Businesses must implement and maintain reasonable data security policies and procedures that are appropriate to the nature of the personal information they collect.
All companies that serve California residents and have at least $25 million in annual revenue must comply with the law. Besides, companies of any size that have personal data on at least 50,000 California residents or that collect more than half of their revenues from the sale of California residents’ data, also fall under the law. Companies don't have to be based in California or have a physical presence there to fall under the law. They don't even have to be based in the United States.
A consumer’s “personal information” is broadly defined to include information that identifies, relates to, describes, is capable of being associated with, or could reasonably be linked, directly or indirectly to a consumer or household. As the law exists currently, personal information includes, but is not limited to, the following:
- Identifiers such as a real name, alias, postal address, unique personal identifier, online identifier, internet protocol address, e-mail address, account name, Social Security number, driver’s license number, passport number, or other similar identifiers;
- Characteristics of protected classifications under California or federal law;
- Commercial information, including records of personal property; products or services purchased, obtained, or considered; or other purchasing or consuming histories or tendencies; biometric information;
- Internet or other electronic network activity information, including, but not limited to, browsing history, search history, and information regarding a consumer’s interaction with an internet web site, application, or advertisement;
- Geolocation data;
- Audio, electronic, visual, thermal, olfactory, or similar information;
- Professional or employment-related information;
- Education information;
- Inferences are drawn from any of the information collected to create a profile about a consumer reflecting the consumer’s preferences, characteristics, psychological trends, preferences, predispositions, behavior, attitudes, intelligence, abilities, and aptitudes.
Specifically excluded from the definition of “personal information” is any information publicly available, meaning any information that is lawfully made available from state, federal, or local government records. “Publicly available” does not mean biometric information collected by a business about a consumer without the consumer’s knowledge.
Like any regulation, the CCPA includes all kinds of specifics to which you must pay attention. There’s plenty of time for that later, but for starters, here are some of the most basic requirements:
- Processes to respond to data subject access requests, including the right to know
- Right to deletion/ to be forgotten
- Reasonable security procedures and practices
Under CCPA, you must look at data security and data governance across your enterprise. Before making any processing decision that involves personal data, you need to put risk under the microscope and focus on the rights and freedoms of the California consumers.
With that in mind, it’s worth spelling out what those rights and freedoms are that apply to California consumers as those turn into responsibilities for your organization.
CCPA puts forth the idea of pseudonymization, whereby identifying data is converted in a way that makes it impossible for unauthorized people to trace it back to an individual. It doesn’t necessarily make the data record completely anonymous, but it’s like translating the identifying information into secret code.
The CCPA poses lots of questions that organizations must consider and raises many distinct data challenges. To begin with, compliance means that your organization must have control and governance of personal data wherever it is across the organization.
That is far easier said than done.
Data, as you know, has proliferated throughout every organization and its business ecosystem. Data diversity is a big trend that works against ease of control and governance, and the requirements of data management and security are made more difficult by the move toward cloud computing and storage.
Here are some questions that many organizations struggle to answer concerning the CCPA:
- Where across this organization and its ecosystem can we find all the relevant and in-scope data to which the CCPA principles apply? Is that data at risk?
- How can our organization keep track of data across the operational ecosystem?
- How can our organization define and manage all of the relevant data assets so we can be certain that we comply with all necessary policies and procedures?
- How can we identify and link all of the in-scope data records to which the CCPA principles apply?
- How can we effectively capture and manage the consumer preferences such as opt-out from sale provided by all of the consumers that we affect? How can we manage changes to each consumer's opt-in/opt-out status, or manage the definition of consent?
- How in the world can we efficiently and effectively respond to subject access requests and requests related to portability and the right of erasure, within the required timeframes
- How do we control access to the relevant data? Do we now remove privacy data when we no longer require it for some relevant function or activity?
The CCPA went into effect on January 1, 2020. However, enforcement by the California Attorney General (AG) started on July 1, 2020.
The California AG will enforce the CCPA and will have the power to issue non-compliance fines. The CCPA also provides a private right of action which is limited to data breaches. Under the private right of action, damages can come in between $100 and $750 per incident per consumer or actual damages if greater. The California AG also can enforce the CCPA in its entirety with the ability to levy a civil penalty of not more than $2,500 per violation or $7,500 per intentional violation.
You could argue that advances in technology are among the root causes of the many issues that the CCPA addresses. The more dependent we become upon data and the technology used to collect, process, and share that data, the more we need to protect data and to ensure that it is not used in ways contrary to the interests of the individual.
The good news is that technology provides solutions, too. In fact, with every challenge comes a new opportunity, and the challenge of CCPA can result in opportunities around your organization’s use of data.
Technology providers have stepped up to make it easier to address CCPA requirements. Informatica brings deep expertise in data management and data governance to help organizations on their path to CCPA compliance. Innovative new data management capabilities make it possible for you to wind up in a better spot after CCPA than you were in before. Informatica has developed integrated and intelligent software solutions for governance and compliance that provide an ideal support system for a CCPA initiative.
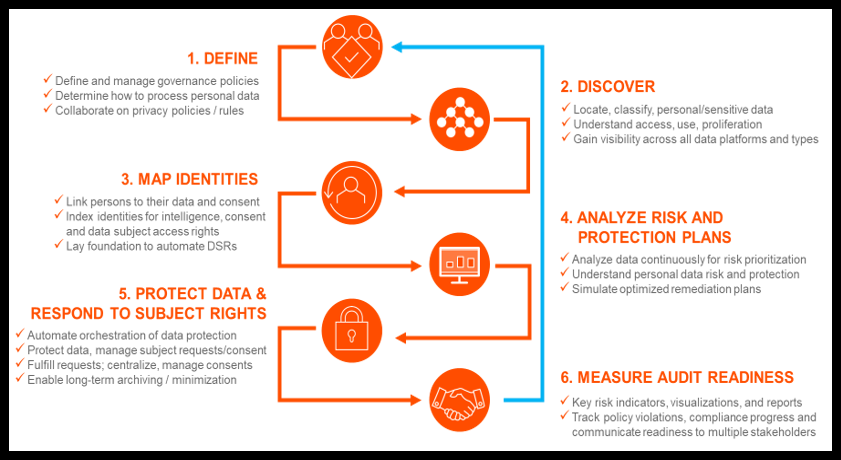
Figure 2. Privacy Journey

Every industry is affected by the digital transformation that has upended the way business is done, as well as the growing amount of data that is collected, processed, and shared. Quite a bit of that data can be attributed to specific individuals, or what the CCPA views as consumers.
The more data your organization deals with, the more challenging it becomes to figure out ownership, control, and management of any given bit of data. You may know of the risks in some cases, but the fact is that there is a lot of risk in what you don’t know, too. If your initiative is going to be as successful as possible, you want an enterprise-wide approach to data governance. The CCPA has an extraterritorial effect. The CCPA applies to any business, regardless of physical presence or place of incorporation, which regularly offers goods or services to persons or entities in California or otherwise purposefully derives benefit from its activities in California.
Technology and Business go hand in hand:
- Policy Definition: This includes business and IT definitions, plus documentation across all operational levels of the business, and logical and physical data and process models.
- Responsibilities: You must determine who owns the data, who uses the data, and what functions within your organization have responsibility for the data’s quality and security.
- Definition of terms and process: This has to do with business processes, key data entities, attributes, systems, quality and controls, standardization, and how the business captures and acknowledges the consent of data subjects to use their data.
- Change process: You need a governed process for definitions, a governed process for change, and overall process governance.
- Linkage to artifacts: This refers to logical-to-physical artifact linkage, producing the technical and business data lineage needed to understand the dependencies, and ensure the quality, of in-scope data.
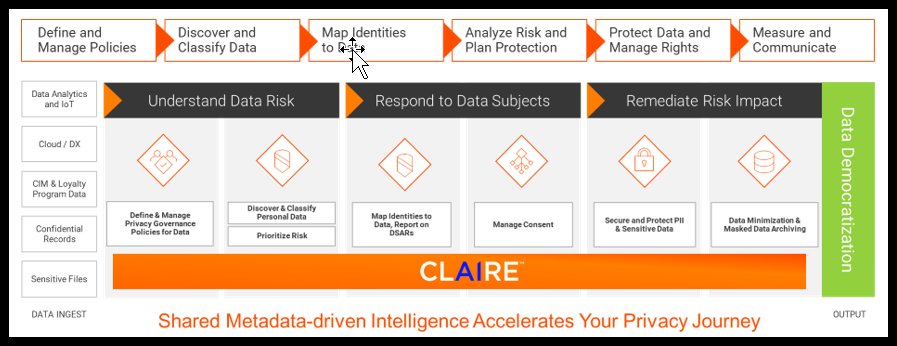
Figure 3. Privacy Process Flow

To succeed in the digital age, your data governance and compliance work need to emerge from siloes and take a holistic approach. That means business and IT functions can work together toward a common goal of Intelligent Data Governance — a concept impactful enough that you can imagine what a competitive advantage it will yield.
Your aim should be to make it quick and easy for all subject matter experts to contribute to the data governance initiative. They’re the ones who should define the processes, policies, and data entities that are part of your holistic data governance capability.
An appropriate data governance initiative features wide-ranging capabilities, beginning with business and IT integration. You’re looking for a collaborative definition of policies, processes, terms, owners, categories, and purpose. It must encompass personal and non-personal data across the entire organization.
Who runs this kind of effort? The answer is lots of key leaders from the various areas affected. Some of the titles to be found in this committee are Chief Privacy Officer, Data Privacy Officer, Data Protection Officer, Chief Data Officer, Chief Information Officer, and Chief Risk and Compliance Officer
You need the right people, for sure, and the right technology. Consider the example of Informatica Axon Data Governance. It’s a solution that lets your non-technical business analysts and business line managers efficiently operate data governance programs. It’s there to provide definition and direction for your intelligent data governance initiative. It’s also specifically designed to unite business and IT views of data, as well as create the link between logical and physical data assets.
- Powerful MetaData: Metadata turns unstructured data into objects that can be separated into the useless, the useful, and the mission-critical. It’s a crucial tool for efficient long-term data management.
- Automated Enrichment: We shine a light on dark data assets, enriching them with valuable metadata to help simplify compliance and secure your data, no matter where it resides.
- Simplified Compliance: Our intelligent data governance solutions are included on a single platform that extends across private and public cloud, reducing the cost and complexity of data governance and compliance reporting.
Different ways in which Data is siloed across an Organization:
- Company Culture: Often departments are siloed from each other, especially in larger companies. Sometimes this occurs because there is internal competition, but often it happens because one department sees itself as separate from another and doesn’t consider where information should be shared.
- Organizational Structures: Unless an organization specifically works to integrate different departments, it’s easy to build layers of hierarchy and management that deter departments from sharing information.
- Technology: It’s not uncommon for different departments to use different technology, making it difficult for the departments to share common information. For example, maybe the Sales team uses Salesforce, but the Marketing team doesn’t have this tool. Yet, it might contain valuable information that the Marketing team could use. An IT survey showed that most companies have between 1-200 applications for their different departments. Consider how unwieldy it can be to find information when you have so many different sources.
- Inability to get a comprehensive view of Data: If your data is siloed, relevant connections between siloed data can easily be missed. Suppose, for example, the Marketing team has excellent data on which Marketing campaigns attracted a lot of attention in geography, whereas the Sales team has information about sales in that same geography. What if you could bring that information together? Imagine how much clearer the relationship between Marketing campaigns and sales would be.
- Wasted Resources: Consider what happens if you have a database with customer information for the Marketing team and a separate one for the Sales team. Much data is duplicated between these departments. It costs money to store all this data, and the more data a company stores, the less the organization can spend on other requirements.
- Inconsistent Data: In Data Silos, it’s common to store the same information in different places. When this happens, there is a high chance that you will introduce data inconsistencies. You might update a customer address in one place and not another. Or, you might introduce a typo in one set of information. When the data is in one place, you have a much better chance of maintaining the correct information.
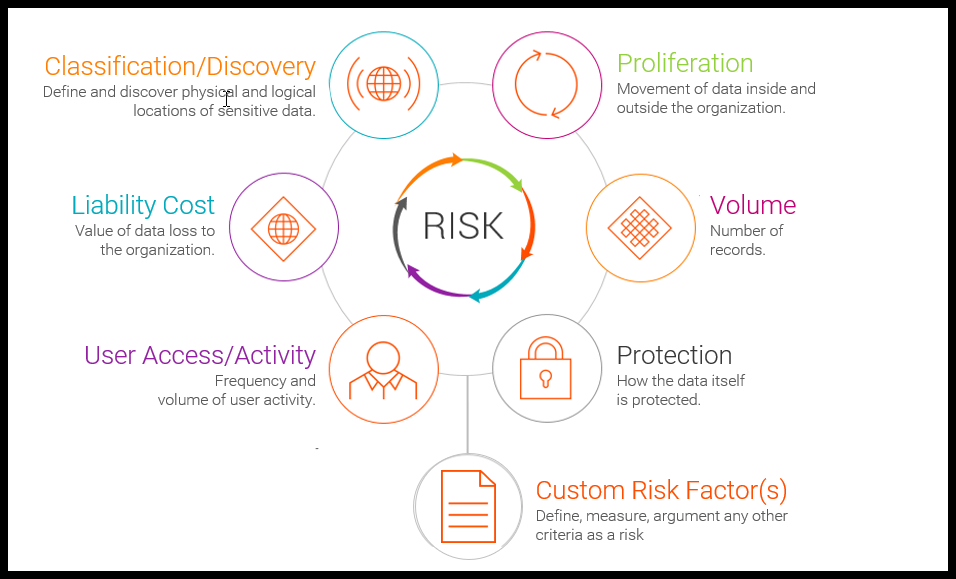
How is the risk score calculated? Many factors determine the level of risk posed by a set of data:
- User access and activity: How frequent is the user activity involving this data, and how much activity is there?
- Proliferation: How much do this data move across geographies, departments, and data stores?
- Data volume: How many sensitive or personal data records are there in this set?
- Liability cost: How much does the organization stand to lose if this data is lost or breached?
- Sensitivity level: Is the data considered confidential? Is it only for internal use?
- Protection: What controls
Figure 4. Risk Analytics

Capabilities of Intelligent Data Privacy:
- Data Policy Definition: This capability gets into both business and IT definitions, as well as vague data and policy conflict.
- Automated Data Discovery: This capability is about finding relevant in-scope sensitive or personal data on the first pass, followed by continual monitoring, plus the classification of data and integration of supporting systems. Data must be defined in context, with intelligent policies that identify whether a combination of specific data elements (such as name, email, and national ID) can be combined in any data store to identify the privacy data of CCPA subjects.
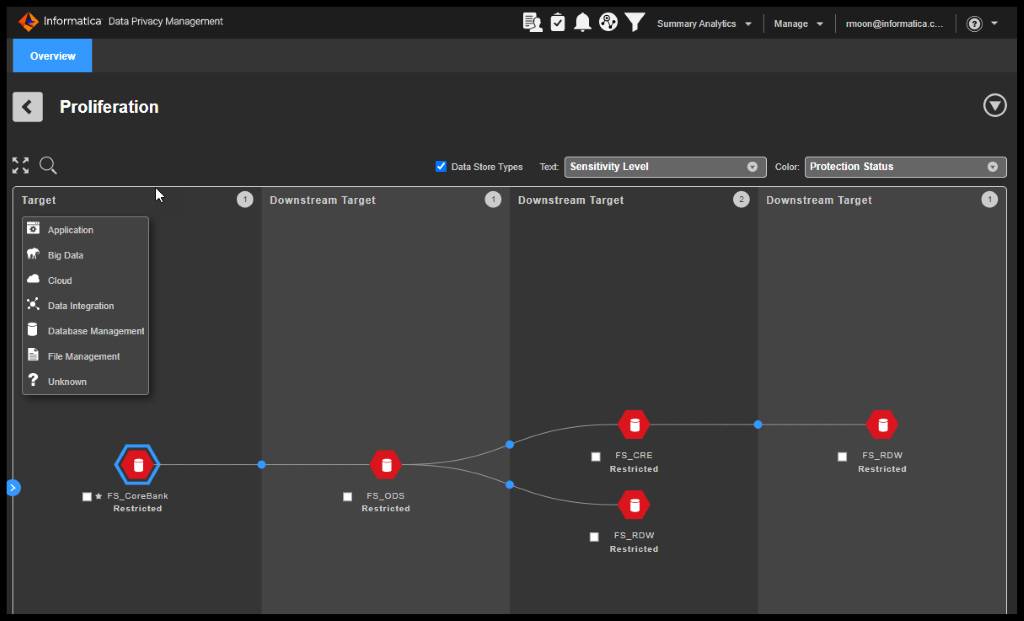
- Data Proliferation Analysis: Data tends to move around, which is what proliferation refers to. It isn’t only a matter of finding out where the data is. You need to know where it goes and what new sources of data are emerging.
- Data Risk Scoring: This considers the factors listed earlier, including the movement of data, proliferation, access, volume, value, and prioritization. This capability should include planning, history, and score monitoring over time. Monitoring would include excess access, anomalous user behavior, and cross-border data transfers.
Figure 5. Data Security Dashboard
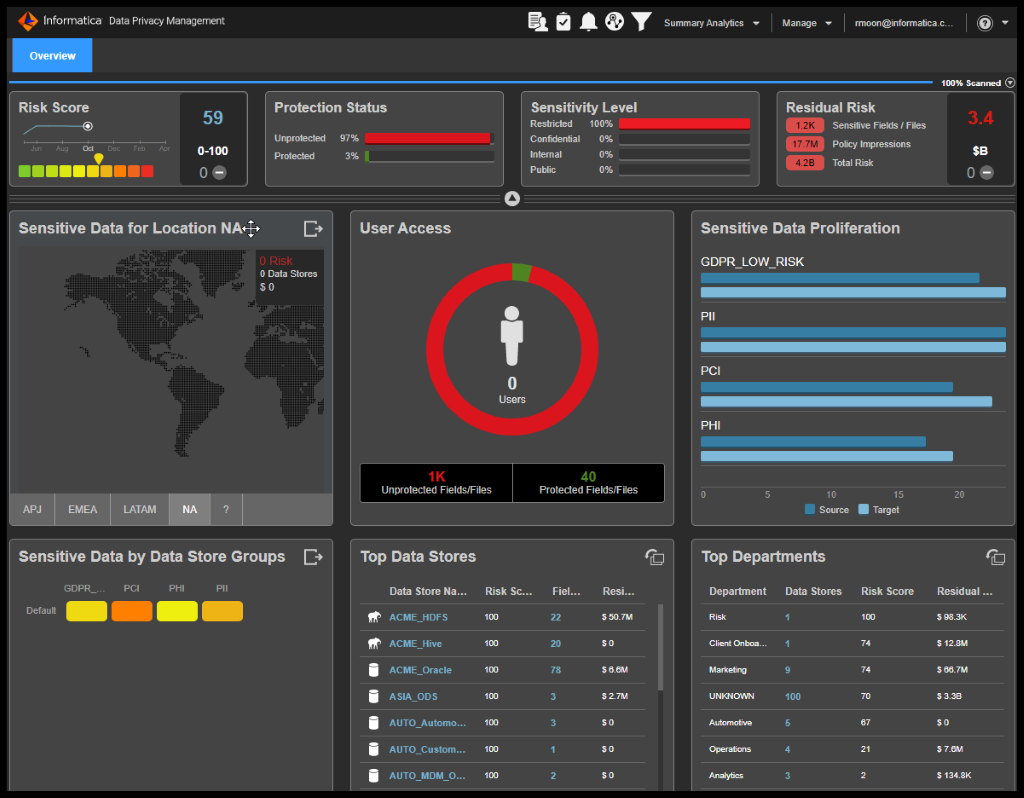

Figure 6. Data Proliferation

Introduction:
Complying with CCPA may require a lot of process and procedure as you ensure that you can answer data subjects’ requests and implement their rights. There’s also a fair amount of technology because all of the data involved must be as secure as it can be.
Security is certainly a technological matter, in terms of building defenses against hacking. But in the end, much of it is a matter of creating controls to ensure that only the right people can access sensitive or personal data. This chapter focuses on the need for properly restricting access to the data you’re holding on protected individuals. It describes helpful data protection controls and outlines technology solutions.
Why Data Protection Controls?
Of the requirements of the CCPA, one of the most basic tenets is protecting your data from being accessed by unauthorized users. That calls for some serious data security controls.
To begin with, from an IT perspective, you face various requirements that privacy data be encrypted, access-controlled, removed, masked, or pseudonymized. It covers data being used in a wide variety of ways, from internal processes, customer services, and order processing to analytics and reporting. Your concerns about data protection also cover data related to testing and development, activities that bring their own sets of issues and challenges.
In practice, ensuring effective data security means reviewing for compliance purposes all the applications that contain or access personal data. These applications need tight data access control for personal data at a user level.
Consider production data. Various people might have access to the data, from administration to product support to app users to partners. Some are authorized, but some are not, and the app infrastructure must remain as is. Because you have unauthorized users in the mix, you would want to mask sensitive or personal data to prevent unauthorized access, through what’s known as Dynamic Data Masking.
Data for analytics, testing, and development data, on the other hand, involves interactions with data analysts, data scientists, and testers, and developers, and potentially no one is an authorized user. Your goal is to remove any risk of sensitive or personal data access, so an effective approach is to fictionalize data for testing or research purposes and permanently change sensitive or personal data. Persistent data masking is the name of the game.
Controls Must Be Complying:
How you’ll protect your organization’s data and ensure that you have the appropriate controls? How do you gain the kind of access control you need to protect the in-scope information of data subjects? By enabling strong and sophisticated security controls. Your Chief Legal Officer, CIO, and Chief Data Officer should be part of the solution to this dilemma. As for the required capabilities, you need enterprise-wide protection and controls over data. These data controls must cover access controls, data deletion and retention, data masking, archiving, and pseudonymization.
The below technology helps with protection:
- Risk analysis input: You’ve done the risk scoring; now use it to direct data control methods.
- Orchestration: This musical term refers to the ability to schedule and coordinate data protection tasks in accordance with identified risks and ongoing monitoring of unsafe access or conditions.
- Data security controls: These include static or dynamic masking, pseudonymization, role-based access controls, encryption, and tokenization.
- Change/update history: You’re comparing the application against source systems, the record masking or archiving outcomes against a consent record, and generating an audit trail for evidence.
- Archiving: This activity takes data out of production systems and archives it, logs the activity to provide evidence, and moves sensitive or personal data offline to prevent accidental usage or access.
Informatica weighs in with powerful solutions that help with privacy and the security of data assets. You can use Persistent Data Masking and Dynamic Data Masking to help automatically limit the number of people and systems that have unrestricted access to personal data. Informatica’s Data Privacy Management, meanwhile, provides extensions to Persistent Data Masking for protection. Data Archive helps organizations remove data that is no longer needed for business operations but could pose privacy risk if exposed. It also helps support the data minimization principles outlined in the CCPA. It’s tremendously helpful to build this kind of automation into data masking. You reduce the risk of personal data breaches and make it a whole lot less likely that unprotected personal data finds its way out to an accessible environment.
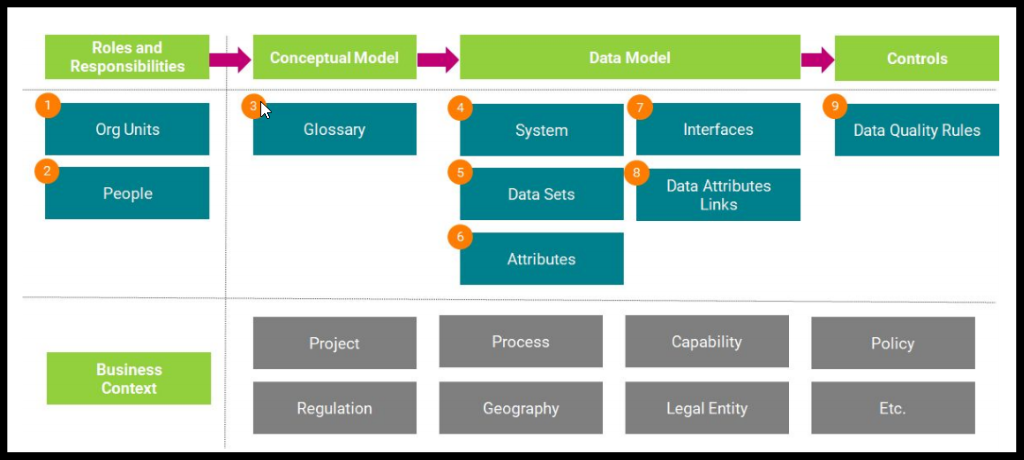
The CCPA Accelerator has prefilled templates with a sample of data mainly to showcase how the “Sensitive Data” moves across the Onboarding Process. Each template defines the facets and relationships between the facets. Mainly concentrated on importing the CCPA regulation body and policies related to the CCPA. Facets that are targeted for this accelerator are Glossary, Regulation, Policy, System, Datasets, Attributes, People, Role, Process, Legal Entity OrgUnit, and Data quality as well.
Templates for different facets like glossary, regulation, Policy, people, system, Datasets are straight forward. These templates import the respective sample data to each facet. The other set of templates builds a relationship between the facets and adds the stakeholders responsible for the asset. The template has another subprocess which helps to build a proper Onboarding process example like Client registration, KYC check, and so on. Process templates have the capability of attaching other subprocesses as well.
After the complete import of the templates, the Onboarding process example takes you to the demoing part of how sensitive data moves across the entire process. Overlays in the process facets show:
- Related Glossaries
- Affecting Systems
- Responsible Stakeholders
- Legal Entity processer and contributors
- Related Policies
- Data Quality results
Along with this sample process example, there will be an exercise with another tool called “Data Privacy Management” that helps an organization to check whether the sensitive data is Protected and what the Risk score, Risk Cost, and Security Levels of the Datastore are. The tool has the capability of masking sensitive data with the privacy rules applied. With the help of a privacy dashboard shown to the Business users in Axon, it makes users immediately take actions based on the result. The Risk Score, Protection status, and Sensitive Levels are visible at the process overlays for the system.
The DSAR reports can be generated with the help of DPM and a sample report is given in this accelerator. To Generate the DSAR one must create the Subject registry for the resource. The sample files required to generate the Subject Registry are included in the Accelerator.
The Accelerator covers the main use cases like:
- SRR (Subject Rights Requests)
- DSAR (Data Subject Access Request)
- RTBF (Right to Be Forgotten)
- Right to Rectification
Figure 8. Loading Assets – Object Dependencies

CORPACME Inc. is one of the largest banking and financial services organizations in the world. CORPACME's international network comprises around 6,000 offices in over 75 countries and territories in the USA, the Asia-Pacific region, the Americas, the Middle East, and Africa. CORPACME Bank Inc. is one of the three major clearing banks in the USA and is a wholly-owned subsidiary of CORPACME Holdings. The business ranges from the traditional High Street roles of personal finance and commercial banking to private banking, consumer finance as well as corporate and investment banking. Across all brands, the bank operates some 1800 sites in North America.
The CORPACME has its head office in San Francisco, California.
CORPACME is a data-driven organization. It is focused on implementing CCPA.
Jacob Smith is the Data Protection Officer in CORPACME.
As a DPO he is responsible for overseeing a company’s data protection strategy and its implementation to ensure compliance with CCPA requirements.
Barb Bernardini (Data Governance Officer) provided the Data Governance framework – Axon, Data Privacy Management, and Persistent Data Masking to be leveraged. Jacob Smith collaborated with Legal Team to address the CCPA regulatory policies and started defining the corresponding processes, systems, glossaries, datasets, and attributes in Axon required to meet the compliance requirements.
Figure 9. Informatica Data Governance Framework for CCPA

How to handle government policies:
- Create policies that define CA residents’ data.
- Map business processes and link to systems.
- Define what data is collected and its purpose.
- Identify data that is shared with 3rd parties.
Jacob Smith being the DPO works with CORPACME’s Legal Counsel to “CREATE ACTIONABLE PRIVACY POLICIES” along with Process Steward. He wants to see that the process is legally exposed and wants to make sure that have evidence to show that they have implemented the policies and process to ensure that should meet the obligations imposed by CCPA principles. He logs in to Axon and makes sure that he has all the privileges to access the rest of the data.
He now searches for CCPA Policy with the help of Unison search and looks for the linked Glossary and how it is linked up to personal data or PII data like the First Name, Last Name, Gender Data of Birth, etc. and he can see the dashboard and the dashboard tells him how much has been approved, Axon Status and Security Classification.
Figure 10. Glossaries linked to Sensitive Data
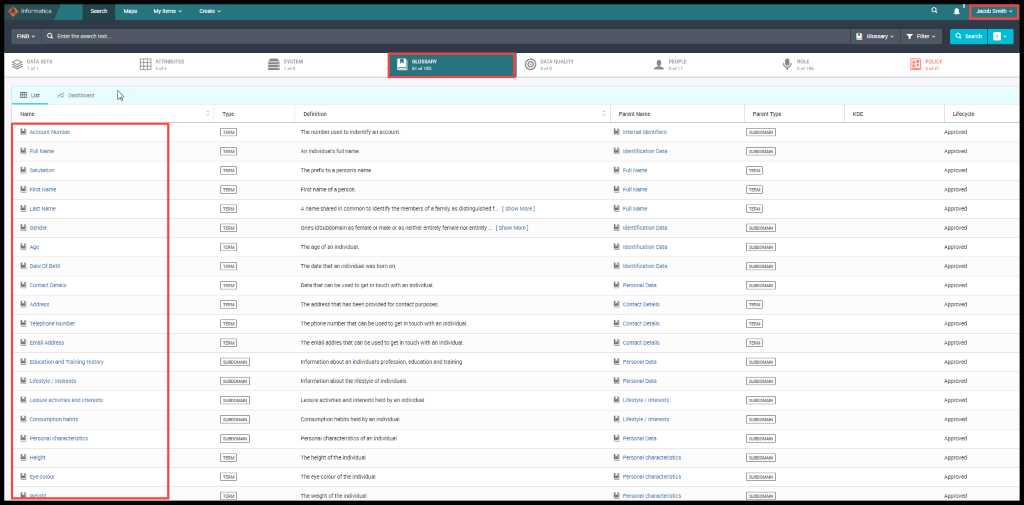

Figure 11. Glossary Dashboard
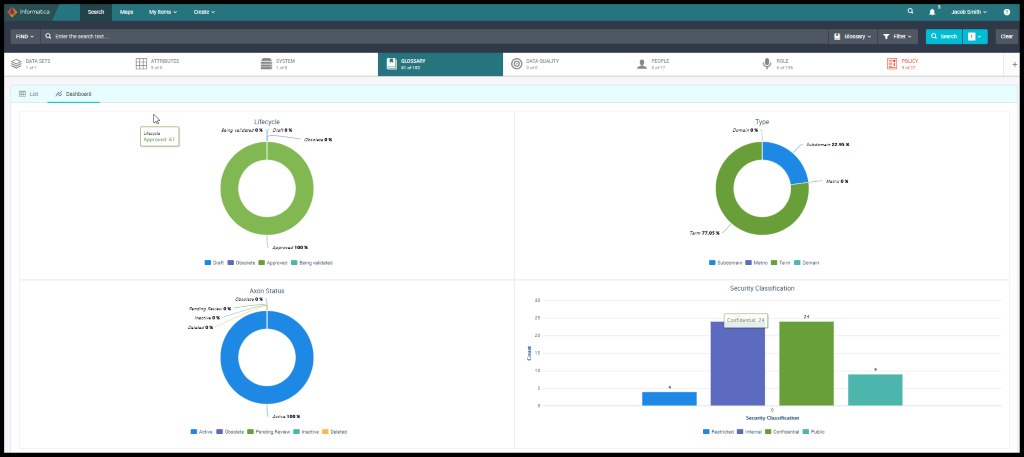

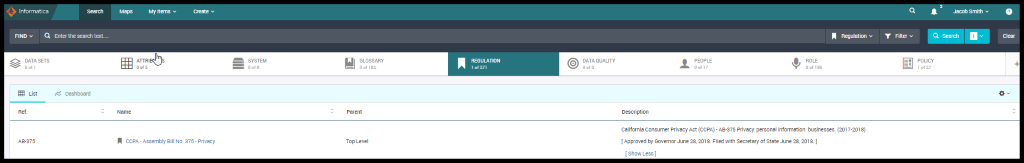
Figure 12. CCPA Regulation

Now Jacob Smith wants to understand the components added in the CCPA regulations for this DPO, selects the Regulation facet and selects the CCPA, and navigates to the Components and sees all the Articles area added to the CCPA regulation.
Figure 13. Components of CCPA Regulation
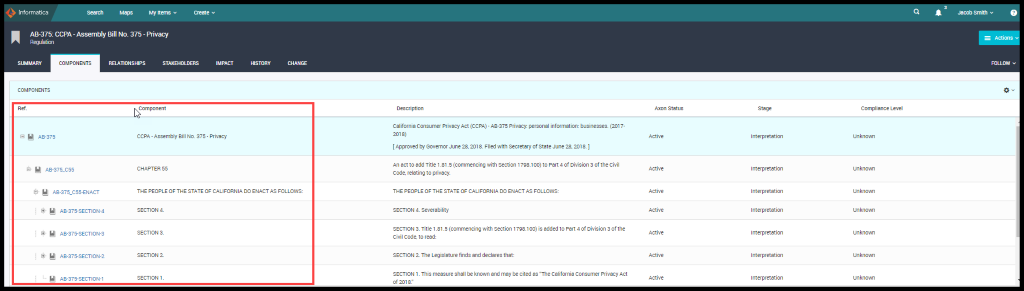

CCPA regulation is external and has been defined with Articles and, he now wants to understand how this regulation has impacted the policy. Hence the CCPA policy is linked to the CCPA Regulation.
CCPA policy is an Axon asset and it has a better description. It also has the link below that takes you to the table of contents in the Articles. Components of this GDPR policy describes all the policies.
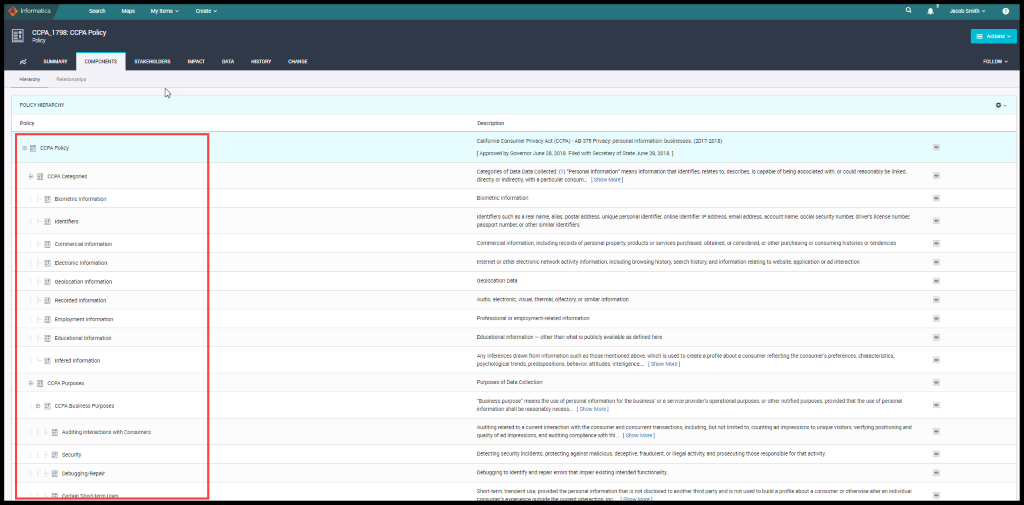
He has decided the best way to implement the CCPA program is to categorize all the purposes of processing and as it is defined in the CCPA.
Figure 14. CCPA Policy Definition

Figure 15. Sub policies of CCPA Policy

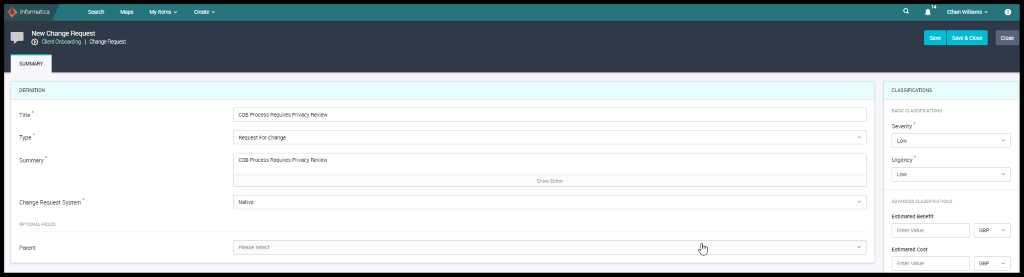
Jacob looks for the process which conducts the “Data Privacy Impact Assessment (DPIA)”. DPIA says that how the personal/Sensitive data is processing across the process. He asks the process owner to act on the Client Onboarding process to check whether the client data is treated appropriately under CCPA.
Ethan Williams being the Process Steward logs a change request saying COB Process Requires Privacy Review.
Figure 16. Change Request

Once the change request is saved then Williams selects the workflow and clicks on “START”.
Here is the workflow diagram:
Figure 17. Workflow Selection
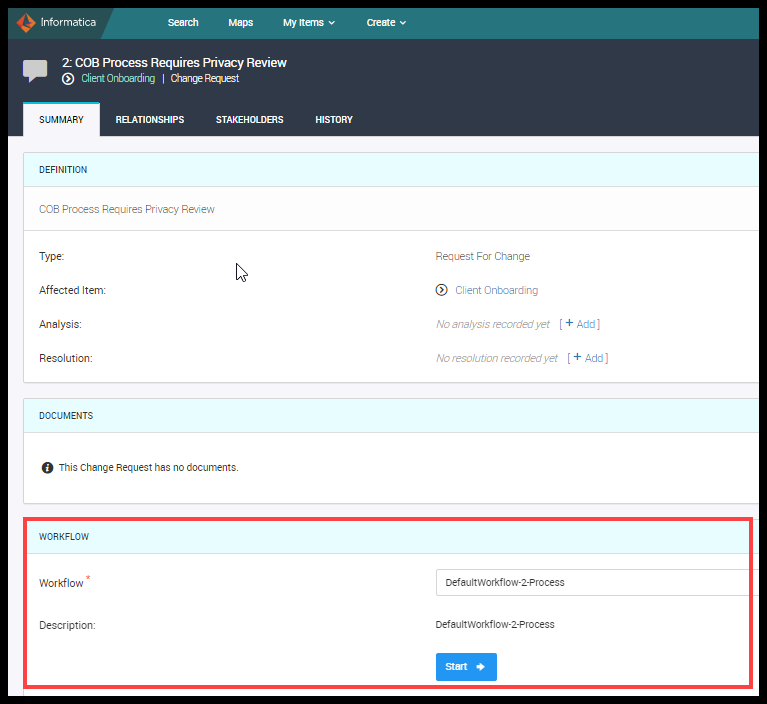

Figure 18. Workflow Diagram

Now the workflow step has moved to the Process Owner – Barb Bernardini and he logs in to Axon and sees the workflow notification under workflow and clicks on the COB Process Requires Privacy Review task.
Figure 19. Workflow Notification
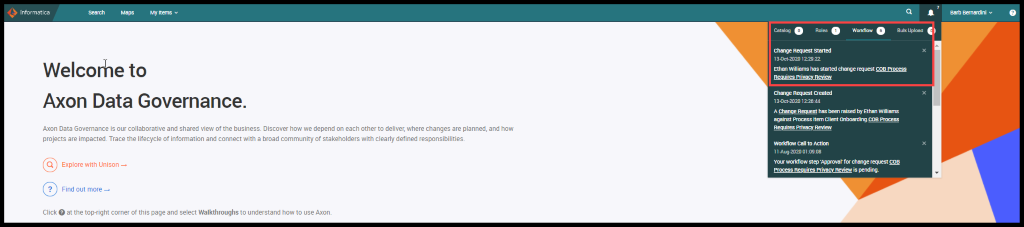

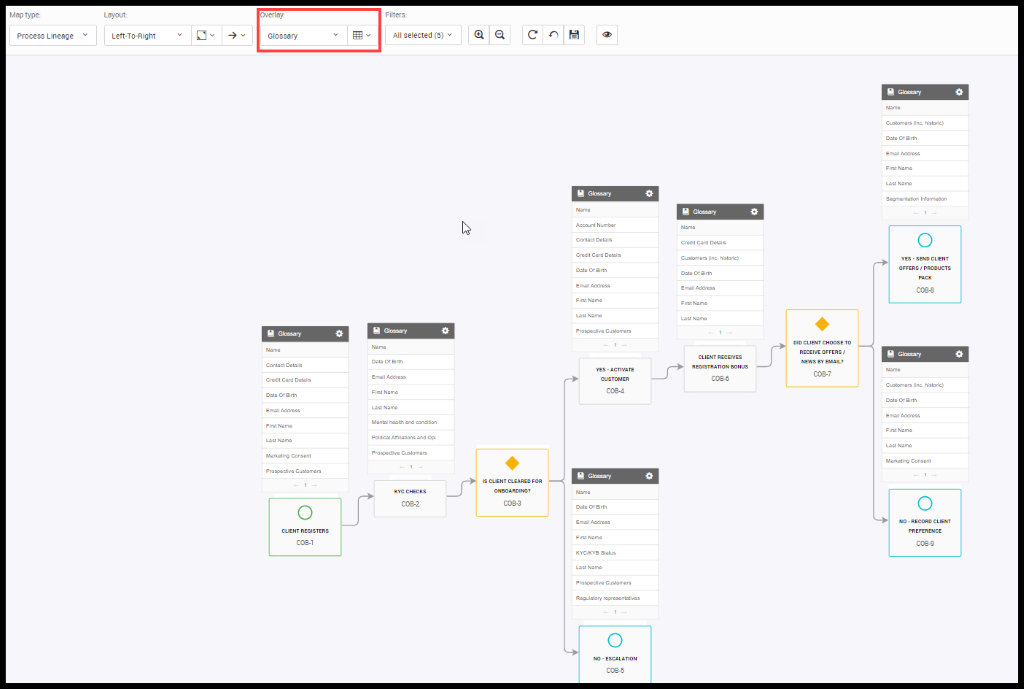
By seeing the details in the workflow Williams opens the Client Onboarding process (COB) by using the Unison search and clicks on the ‘Components’. This shows the complete flow of the COB process and all the sub-processes and the subprocess are linked with the help of the import template.
The process starts from ‘Client Registration’ followed by a KYC check and after condition if KYC is good and moves to Activate the Customer and Client receives registration process and after condition, match Client receives offers in the ‘Yes send client Offers/Products Pack’, If not No record client preference. This is the overview of the Onboarding process.
Figure 20. COB Process Diagram

To see the PII data moving through the process, Barb opens the Glossary overlay. The below Glossary overlay highlighted with Full Name PII data shows the movement through the process. He adds the security classification in the same overlay that shows the data is confidential, protected, or restricted. He sees that there are PII data that is restricted and it’s a special category data and it must be treated even more carefully, and he understands what kind of PII he is dealing with and, how it is moving through the process.
Figure 21. Glossary Overlay in COB Process

How to manage personal and sensitive data:
- Precisely locate and map where CA resident’s data is held.
- Identify how personal data is moving.
- Risk rank data stores for comparison and pinpointing data protection issues.
Data Privacy Management helps you discover, classify, analyze, protect, and monitor personal and sensitive data across the organization. It leverages artificial intelligence (AI) to deliver actionable data discovery and classification, risk scoring, data subject identity capabilities, behavioral analytics, and automated protection in a single solution. It supports structured, semi-structured, and unstructured data in the cloud, on-premises, in big data stores, and relational and mainframe systems.
Johnson and Ethan Williams collaborate to Rapidly locate, map, and understand sensitive data across the Enterprise:
Figure 22. Data Security Dashboard in DPM
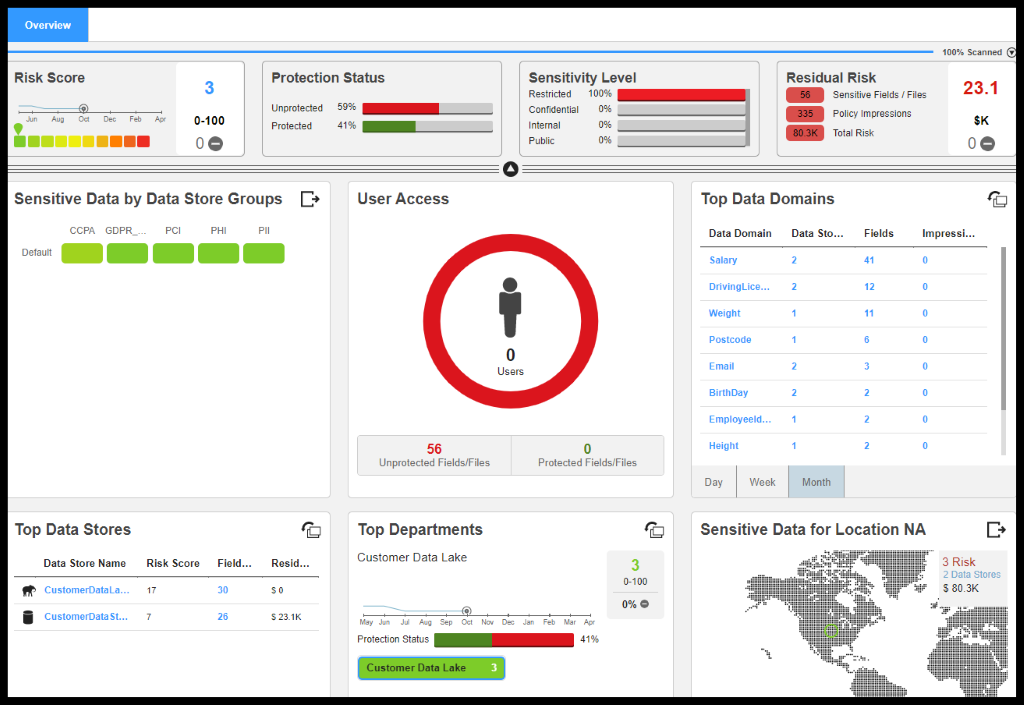

They were able to gain a complete understanding of data, its movement, and its usage in business processes with proliferation tracking and interactive visualizations—both inside and outside the enterprise and between partner and client organizations.
Also, they were able to attain complete sensitive data visibility with dashboards and drill-downs to identify functional and organizational information such as department, application, user, and data storage types:
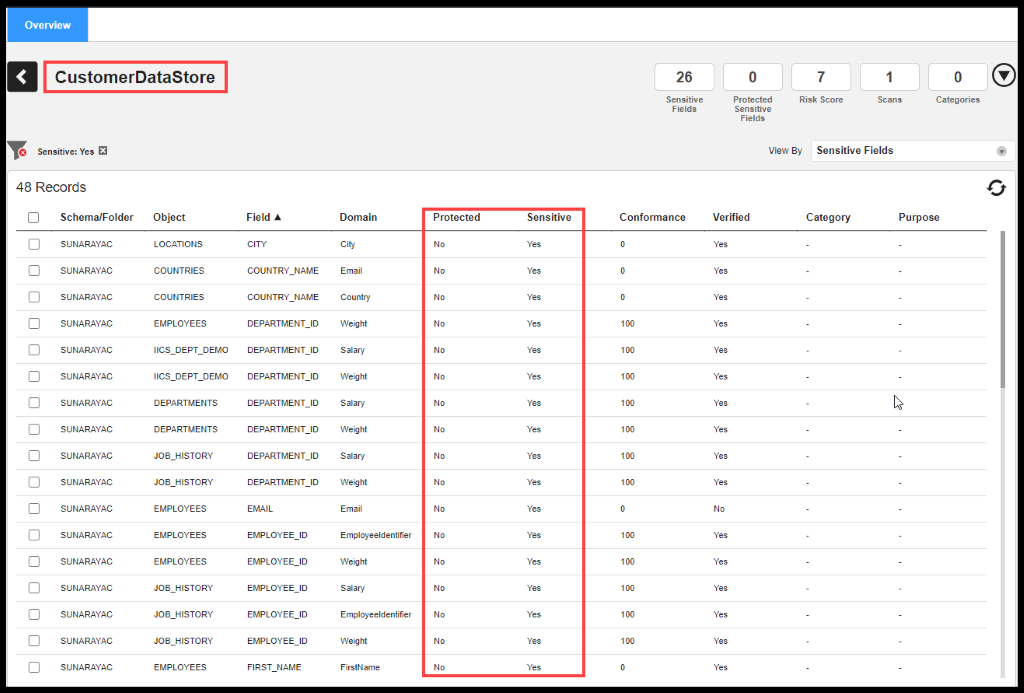
Ethan analyzes the Sensitive Fields captured for “CustomerDataStore” associated with “CCPA” Classification Policy:
Figure 23. Status of Protection and Sensitivity for a Data Store

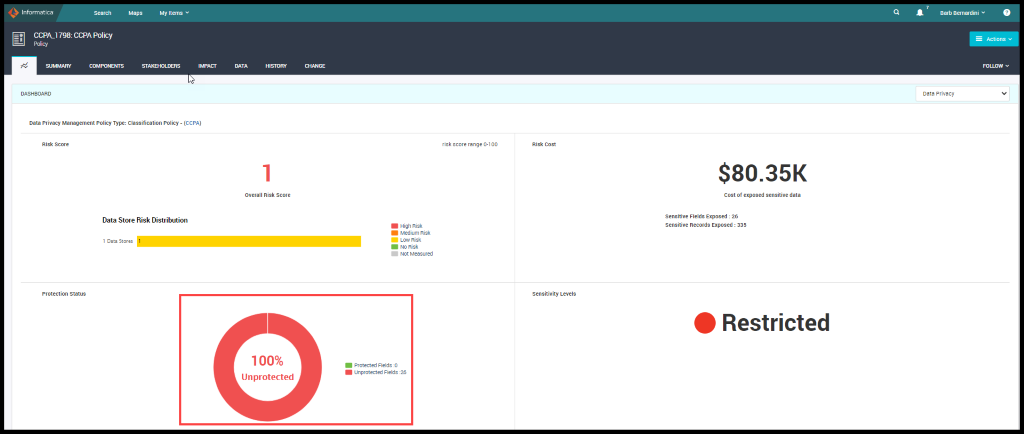
Note: DPM and Axon integration should be taken place and the user must configure the settings of the Classification policy to CCPA policy.
Figure 24. Privacy Dashboard in Axon

How to Map Identities?
- Automated linking of identities to data categories captured on CA residents.
- List/locations of the data stores that contain resident’s data.
- Mapping of resident attributes (data domains) that exist in various stores.
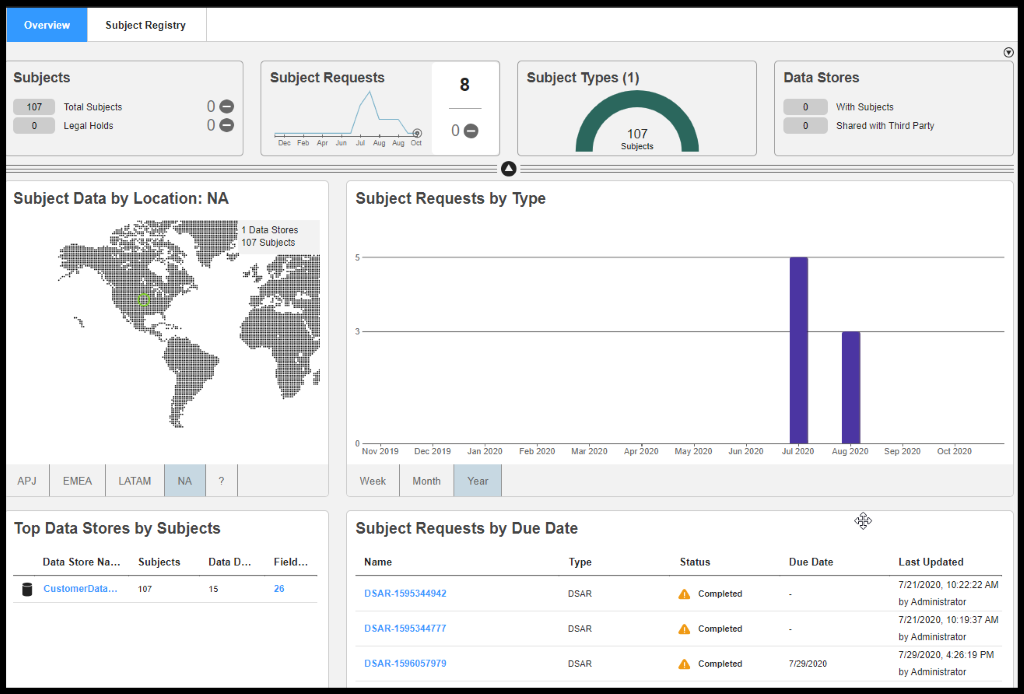
SUBJECT REGISTRY in Data Privacy Management provides identity mapping capabilities that support CCPA data privacy legislation.
Specifically, Subject Registry maps individuals with the data that you maintain on them and provides a detailed report on the location and type of that data.
Access the Subject Registry workspace from the Summary Analytics menu. To quickly locate an individual's sensitive data, search for the individual by name or another identifying detail.
The search panelists one or more individuals that match the search criteria. Determine the correct individual and then access the detailed view to determine the data stores, schemas, tables, fields, and files that contain the individual's sensitive data.
Kevin Feeney is a premium customer with CORPACME. He wants to know where and all his data is residing in CORPACME DATA ASSETS.
He has submitted a request and the Data Protection Office has forwarded his request to Data Privacy Management Administrator. Data Privacy Management Administrator will have to generate a report and respond to DPO’s ticket.
Figure 25. Search for Subject
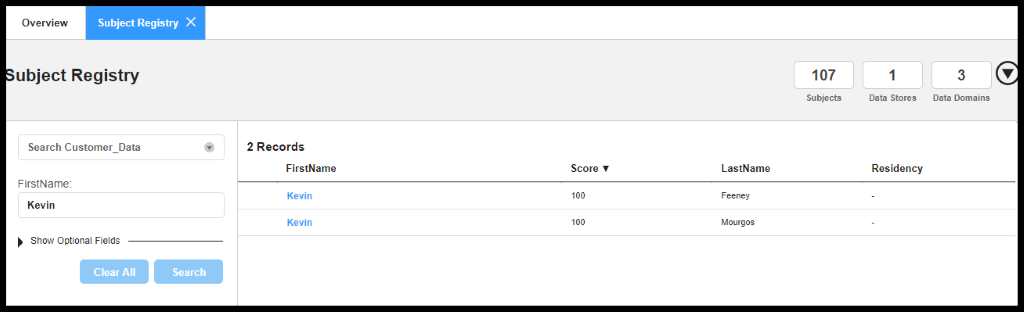

Figure 26. Subject Details along with Data Store
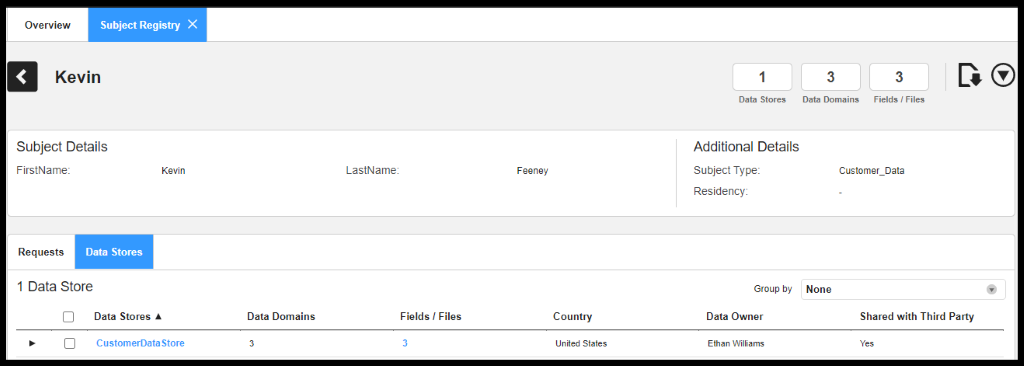

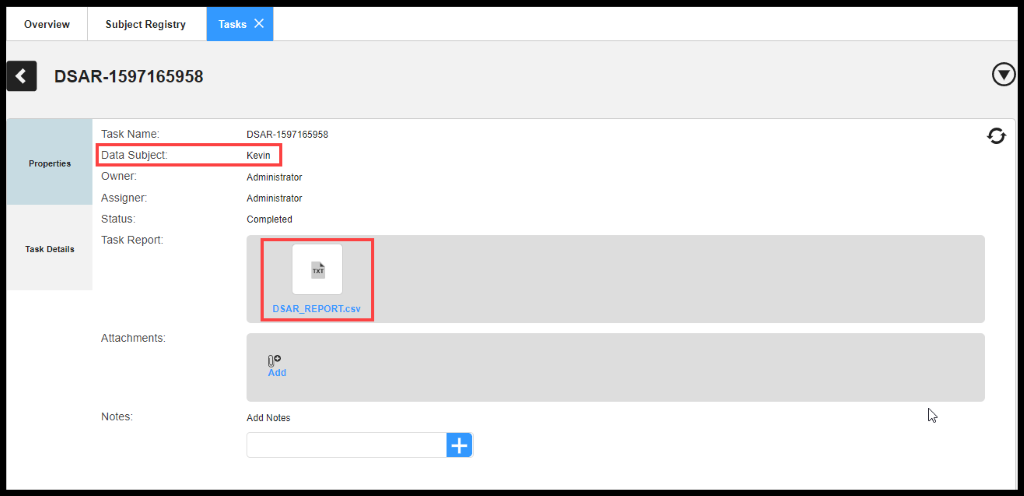
DSAR Report: The Data Subject Access Rights report for Johnson lists all the Data Sources and sensitive fields associated with Kevin Feeney.
Figure 27. DSAR Report

How to handle Data Risk:
- Understand where CA resident’s data is at risk for misuse or unauthorized access, prioritize and plan remediation, particularly concerning data that is subject to breach notification under CA law.
- Identify the security needed for different types of resident’s data.
- Analyze risk based on data properties, policies.
- Simulate remediation to understand outcomes.
- Track risks by an organization, locations, individuals.
Ethan Williams starts Analyzing Risks tries to understand how it is moving through the SYSTEM landscape. And he applies the Risk Score, Protection Status, and the Sensitivity Levels. These are obtained from the Data Privacy Management tool integrated with Axon.
Note: As an example, here, it is considered as one system. If multiple systems are involved, then the user can see the maps with how the PII data is moving through the system landscape.
Note: The same resource is scanned in the DPM to obtain the risk score and protection levels. After applying the masking, the results are shown. After obtaining the PII data and its security levels, he masks the data in Data privacy management and Test data management tools and gives back the results to Axon.
Barb got all the PII data about the process and now he wants to understand who the stakeholders are and who is responsible for all the sub-processes and who is responsible for getting these things done and making sure that good data governance is in place.
Figure 28. Stakeholder Overlay View on Process
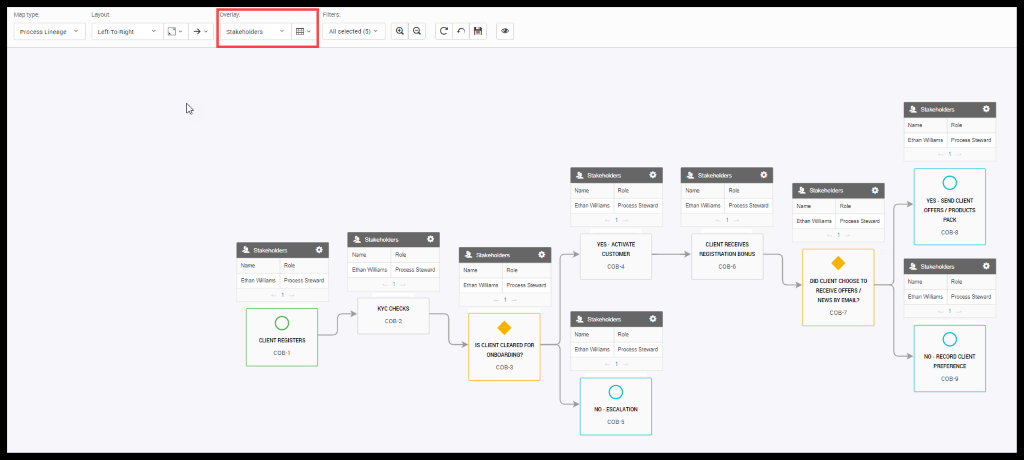

And now he looks at where the data is being used and where it is going by seeing the overlay Legal Entity. As per the article, the organization should know who is using the data and how.
Figure 29. Legal Entities Overlays
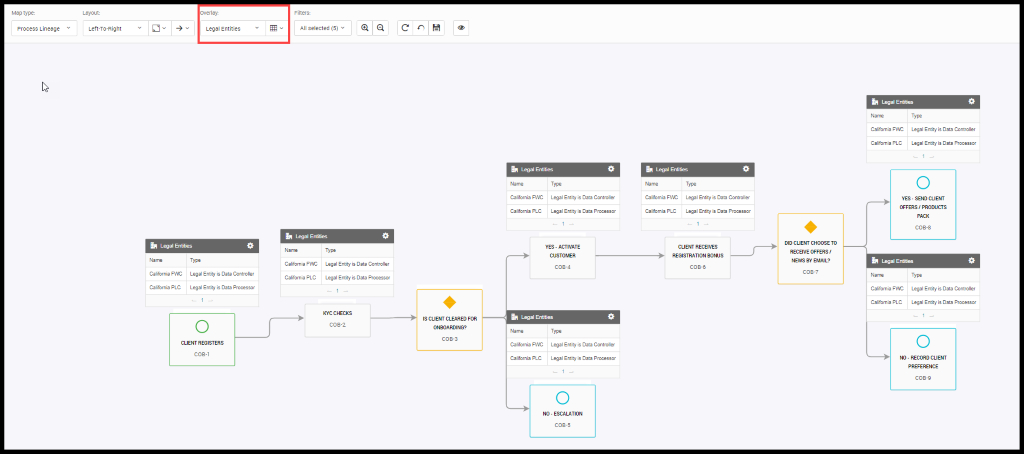

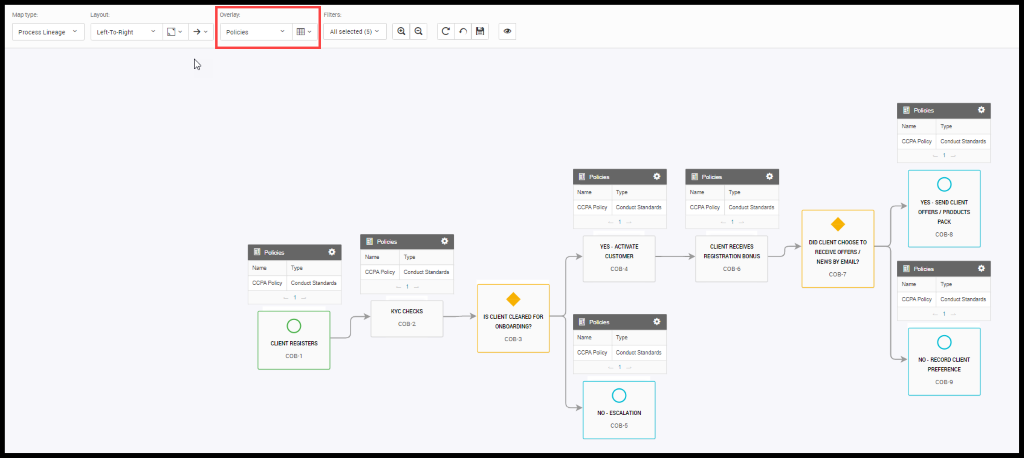
Barb thinks about all these and whether they have the appropriate policies in place as it is going out of CA. To have good governance, the policies must be associated with each process. Now he clicks on the Policies overlay to check what all are the policies that have been aligned to each process.
Figure 30. Policy Overlays

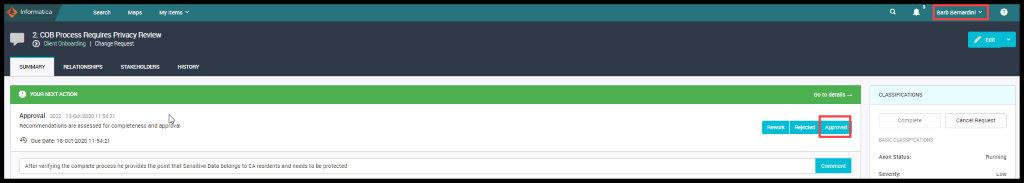
Barb updates the workflow by seeing the entire process results and how the PII data is moving through the COB process and mentions that the PII data is moving out of the CA and hence it is necessary to safeguard the PII data and approves the flow.
Figure 31. Workflow Approval

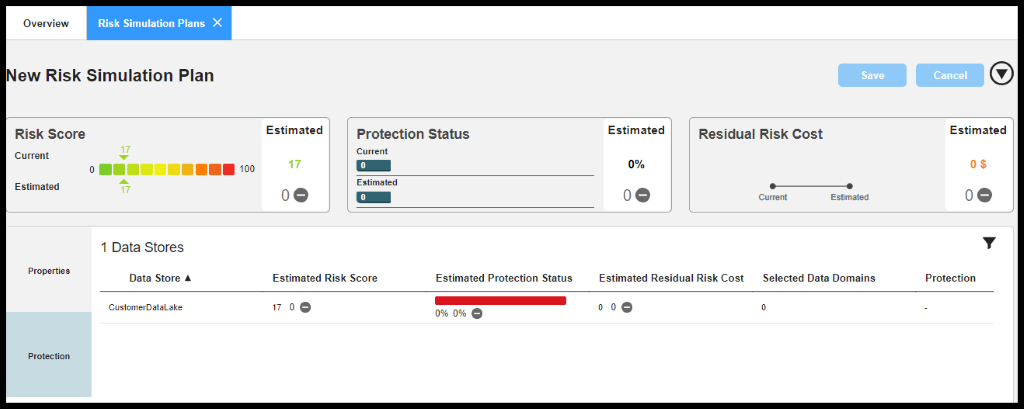
Risk Simulation Plans
You can create and manage plans to reduce the risk score and residual risk cost of unprotected sensitive data domains in one or more data stores. For each risk simulation plan, you can adjust the protection status of sensitive data domains in scanned data stores to simulate the impact on the potential cost to your organization in the event of a security breach.
Figure 32. Risk Simulation Plan

How to configure the RISK Simulation plan properties?
Configure risk simulation plan protection properties for each datastore included in the plan to reduce the risk score and residual risk cost of unprotected sensitive data. On the Risk Simulation Plan Details page, you can select sensitive data domains to protect for each scanned data store included in the plan. The following image shows the risk simulation plan protection properties on the Risk Simulation Plan Details.
Figure 33. Risk Simulation Plan Protection Properties
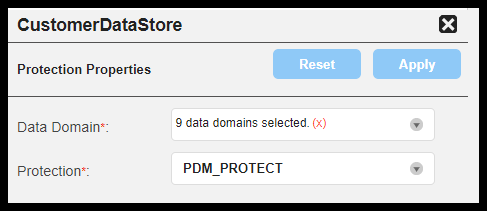

Data Domain: Required. Select one or more sensitive data domains for the selected data store to simulate the impact that protecting data will have on the risk score, protection status, and residual risk cost indicators.
Protection: Required. Select a protection method to simulate the risk impact.
Based on the assessment of the sensitive data now he plans to mask the data.
How to manage subject rights?
- Support requests from CA residents.
- Manage residents’ consents.
- Protect resident’s data in operations, development, and test and analytics
Figure 34. Consent Diagram
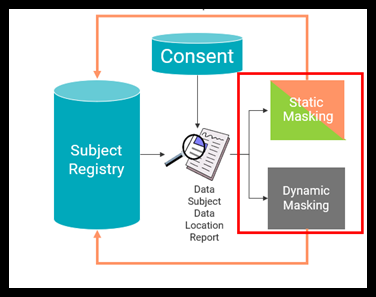

Opt-out from customers can be taken from a third-party tool or Informatica Customer 360. Now Johnson and Ethan with the help of the subject registry will find out what are all the sensitive data and which all tables contain the sensitive data now as per the opt-out taken, and need to protect this data.
Here is the Data Privacy Dashboard from Axon at the CCPA Policy level showing the protection status.
Figure 35. CCPA Policy Privacy Dashboard in Axon
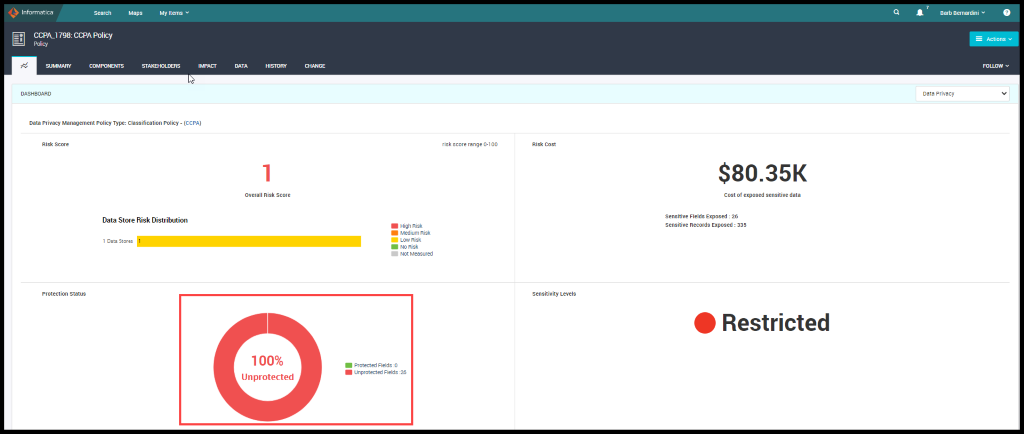

Jacob Smith does a deep dive further on the Protection Status in Informatica’s Data Privacy Management by Data Store. He plans to protect sensitive Data using Informatica’s Persistent Data Masking which is an extension of Data Privacy Management.
Figure 36. Protection Status
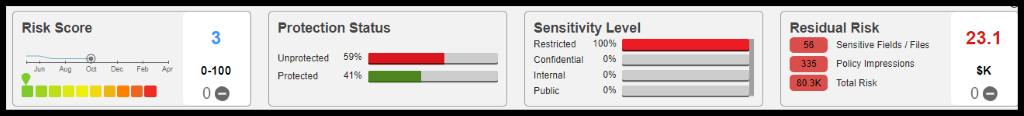

Figure 37. Protection Task Status
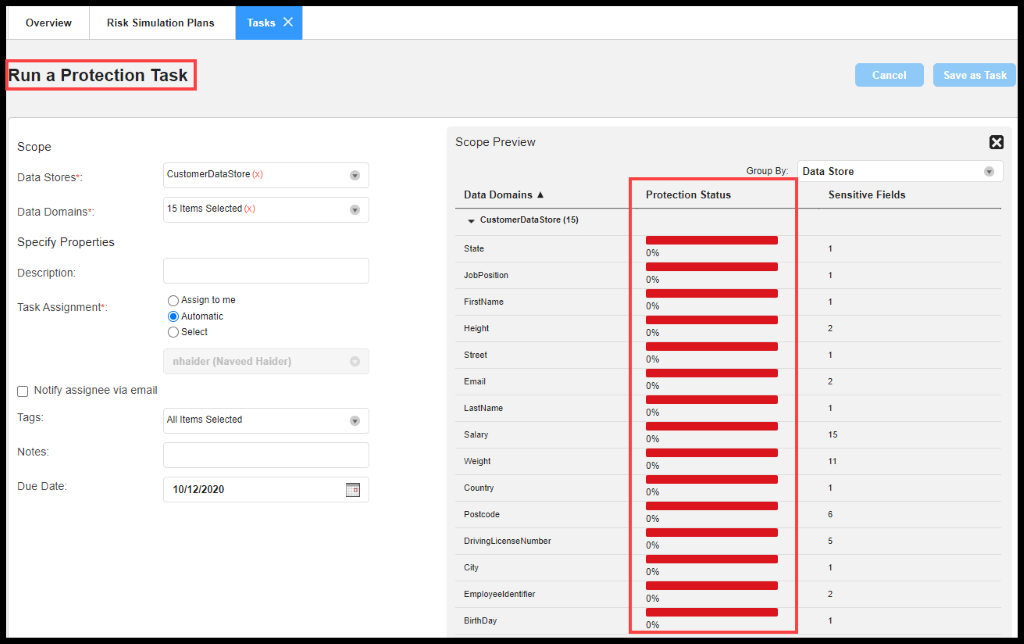

The process which has sensitive data has also been captured to see the protection status.
Figure 38. Sensitive Data in Process
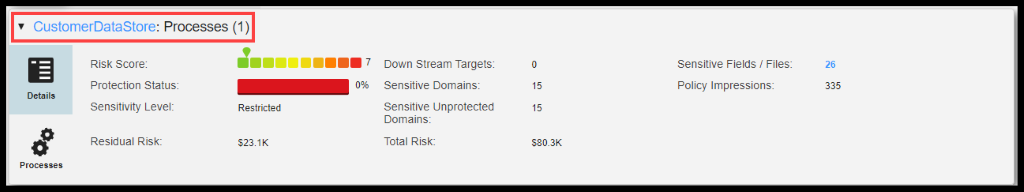

Barb has requested the Administrator to integrate Data Privacy Management with Informatica Persistent Data Masking using Extensions and configure it for executing Protection Tasks.
Figure 39. Extensions
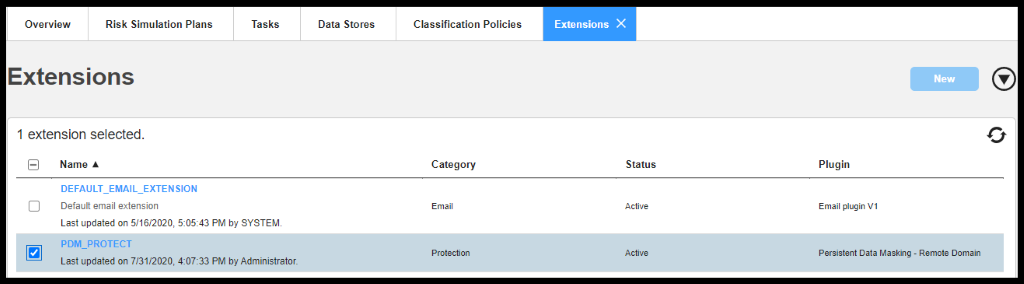

Post Protection task completion, the Administrator notifies Jacob about the results.
Figure 40. Protection Status after Masking

How to measure Audit Readiness?
- Respond to status requests.
- Track CCPA program progress.
- Collaborate across functions and roles.
Jacob Smith & Barb Bernardini as part of the leadership track Compliance Progress and Communicate Readiness to multiple stakeholders, monitors the Protection Status at CCPA Policy in Axon.
Figure 41. Protection Status at Field Level
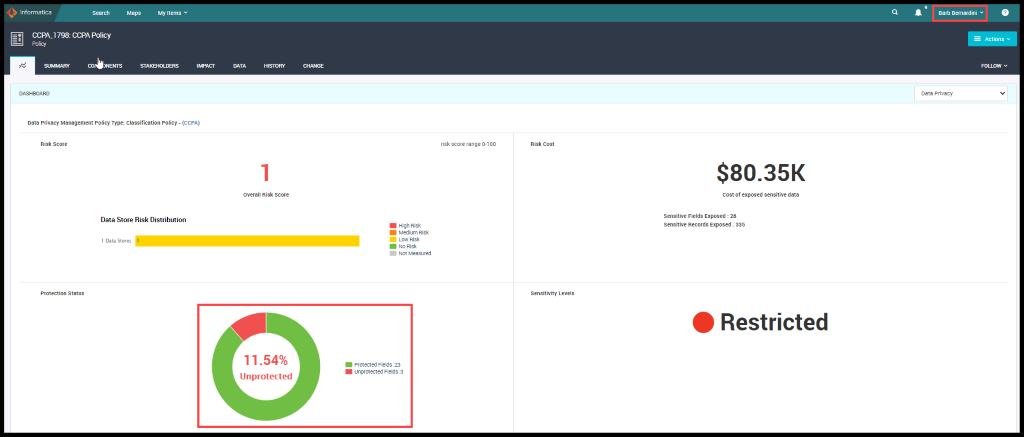

Ethan Williams monitors the Protection Status Deep Dive at Data Store/Field level in Informatica’s Data Privacy Management Reports:
Figure 42. CustomerDataStore
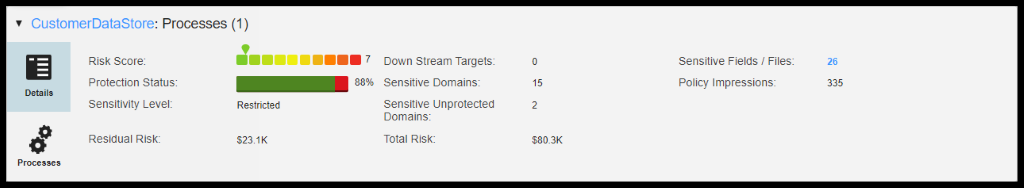

She does notice that the Customer Data Store Sensitive Fields are all Protected in DPM, which automatically gets reflected in Axon at the CCPA Policy level.
Figure 43. Data Security Dashboard in DPM
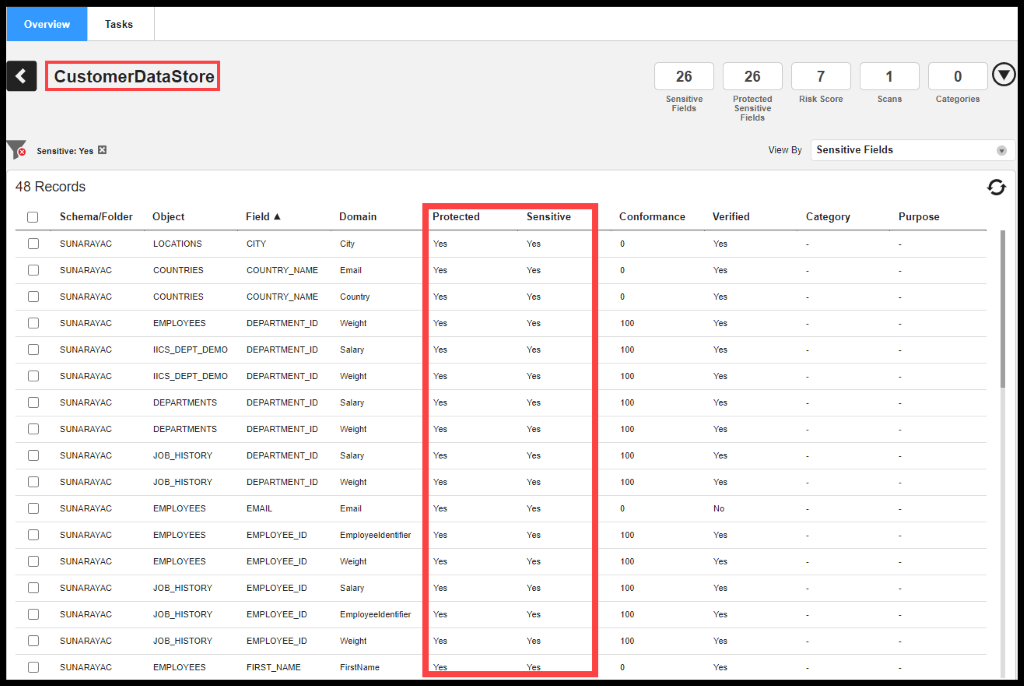

Jacob and Ethan were able to successfully able to meet the CCPA requirements using Informatica Data Privacy and Governance stack.
Figure 44. Data Security Dashboard in DPM
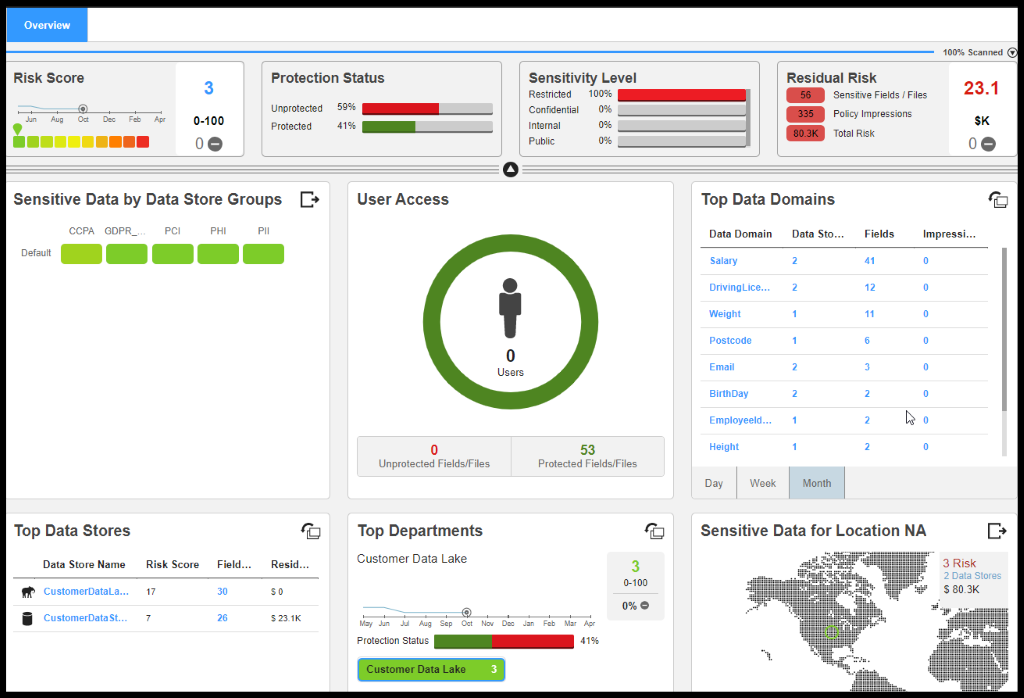

Figure 45. Data Privacy Dashboard in DPM

Configuration Video:
The CCPA Templates enables your organization to create an integrated operational process for maintaining compliance.
In conclusion, CCPA Compliance is an ongoing commitment. Privacy is going to continue to play an important role for consumers and you need to be ready.
